Industry 4.0 Knowledge Graph Ontology
Release 2019-12-04
- This version:
- https://w3id.org/i40/sto
- Latest version:
- https://w3id.org/i40/sto
- Revision:
- 0.8
- Authors:
- Steffen Lohmann, Fraunhofer IAIS
- Irlan Grangel Gonzalez, Fraunhofer IAIS
- Paul Baptista
- Sebastian Bader, Fraunhofer IAIS
- Publisher:
- Fraunhofer-Gesellschaft, FhG
- Download serialization:
- License:
Abstract
The Industry 4.0 Knowledge Graph, I40KG or previously Standards Ontology (STO), represents standards, standardization organizations and standardization frameworks for the Industry 4.0 area.Introduction back to ToC
This documentation presents STO, an ontology to describe standards, organizations for publishing standards as well as standardization frameworks in the context of Industry 4.0.Namespace declarations
| cc | <http://creativecommons.org/ns#> |
| dbo | <http://dbpedia.org/ontology/> |
| dbr | <http://dbpedia.org/resource/> |
| dc | <http://purl.org/dc/elements/1.1/> |
| dcterms | <http://purl.org/dc/terms/> |
| deo | <http://purl.org/spar/deo/> |
| doap | <http://usefulinc.com/ns/doap#> |
| dul | <http://www.ontologydesignpatterns.org/ont/dul/DUL.owl#> |
| foaf | <http://xmlns.com/foaf/0.1/> |
| geo | <http://www.geonames.org/ontology#> |
| lang | <http://lexvo.org/id/iso639-3/> |
| muto | <http://purl.org/muto/core#> |
| oa | <https://www.w3.org/ns/oa> |
| obda | <https://w3id.org/obda/vocabulary#> |
| om2 | <http://www.ontology-of-units-of-measure.org/resource/om-2/> |
| owl | <http://www.w3.org/2002/07/owl#> |
| prov | <http://www.w3.org/ns/prov#> |
| rami | <https://w3id.org/i40/rami#> |
| rdf | <http://www.w3.org/1999/02/22-rdf-syntax-ns#> |
| rdfs | <http://www.w3.org/2000/01/rdf-schema#> |
| schema | <http://schema.org/> |
| skos | <http://www.w3.org/2004/02/skos/core#> |
| sto | <https://w3id.org/i40/sto#> |
| sto_iot | <https://w3id.org/i40/sto/iot#> |
| vann | <http://purl.org/vocab/vann/> |
| voaf | <http://purl.org/vocommons/voaf#> |
| voag | <http://voag.linkedmodel.org/voag#> |
| xml | <http://www.w3.org/XML/1998/namespace> |
| xsd | <http://www.w3.org/2001/XMLSchema#> |
Industry 4.0 Knowledge Graph: Overview back to ToC
This ontology has the following classes and properties.Classes
- Admin Shell Sub Model
- Alliance of Industrial Internet Architecture Classification
- Architecture Description
- BDVA Concern
- Business Cycle SCM
- Connectivity Layer
- Connectivity Layer
- Data Sharing Initiative
- Domain
- Edgecross Layer
- Fiware Chapter
- i io t consortium
- IDS RAM Layer
- IDS RAM Layer
- IDS RAM Perspective
- IDS RAM Perspective
- IIRA Crosscutting Function
- IIRA Crosscutting Function
- IIRA Functional Domain
- IIRA Functional Domain
- IIRA System Characteristic
- IIRA System Characteristic
- IoT-A Perspective
- ISA 95 Level
- IVI Layer
- Layer
- Layer
- License Document
- NGSI Context Information Management API
- OCF Framework Block
- Product Development Life Cycle
- Production System Life Cycle
- RAMI Hierarchy Level
- RAMI IT Layer
- RAMI Life Cycle Layer RAMI Life Cycle Layer
- Standard
- Standard Classification
- StandardOrganization
- StandardPart
- Standarization Framework
- Technical Report
- Technical Specification
- Technology
- Viewpoint
- x-road Section
Object Properties
- alignes With
- alignes With
- belongs To
- frames
- frames
- has Available Language
- has Classification
- has Developer
- has domain
- has File Size
- has Headquater In
- has ICS
- has motivation
- has Previous Version
- has Publisher
- has Target Concern
- has Target Concern
- has Technical Committee
- has unit
- is Component Of
- is Described in
- is Implementation Of
- is member of
- related To
- supports
- use Structure Of
- uses
- was Generated By
Data Properties
- has Abbreviated Name
- has Domain Name
- has Edition
- has Formation Date
- has Implementation Format
- has numerical value
- has Objective
- has official resource
- has Ontology
- has Pages
- has Publication Date
- has Stability Date
- has Status
- has tag
- has Task
- Org Name
- std Part Name
Named Individuals
- 6LoWPAN
- Access Policy
- Access Rights for IoT-Cloud
- Accountability
- Actuation
- Adaptability
- Administration Shell
- Administration Shell Header
- Aeron
- agility
- aii data anno
- AII Data Classification
- AII Industrial Internet Architecture
- aii network anno
- AII Network Classification
- aii security anno
- AII Security Classification
- Alliance Industrie du Futur
- Alliance of Industrial Internet
- Alljoyn
- AllSeen Alliance
- AMQP
- anno actuation
- anno aii classification
- Anonymity
- Arrowhead Framework
- Arrowhead Project
- Artificial Intelligence
- Asset Management
- Authentication
- authorization
- Auto Scaling
- Autonomous Communication
- Autonomous Configuration
- Availability
- Awareness
- Bandwidth
- BDV SRIA European Big Data Value Strategic Research and Innovation Agenda version 4.0 October 2017
- BDVA Cloud and High Performance Computing
- bdva cloud and high performance computing anno
- BDVA Communication and Connectivity
- bdva communication connectivity anno
- BDVA Concern
- bdva concern anno
- bdva cyber security trust anno
- BDVA Cybersecurity and Trust
- BDVA Data Analytics
- bdva data analytics anno
- BDVA Data Management
- bdva data management anno
- BDVA Data Processing Architectures
- bdva data processing architectures anno
- BDVA Data Protection
- bdva data protection anno
- BDVA Data Sharing Platforms
- bdva data sharing platforms anno
- bdva data visualization and user interaction anno
- bdva development engineering anno
- BDVA Engineering and DevOps
- BDVA IoT CPS and Edge Computing
- BDVA SIRA
- bdva sira anno
- BDVA Standards
- bdva standards anno
- bdva things assets sensors actuators anno
- Big Data Applications
- Big Data Value Association
- Blockchain
- Bluetooth
- BPM
- Business Context
- Business Transactions
- Business Value
- cardinality of data sources
- Cardinality of Participants
- CEP
- Certification
- Cloud Computing Capability
- cloud connectivity
- CoAP
- communication
- Compliance
- Confidentiality
- Connectivity
- Constrained Devices
- Context Awareness
- Cost Efficiency
- Cross-domain Identity Management
- customer
- Customization
- Customization
- d i n e n 50128
- d i n e n 50159
- d i n e n i s o 13849
- d i n e n i s o i e c 17025
- d i n i s o 14638
- d i n s p e c 16593 p1
- d i n s p e c 92222
- Data Access
- Data Access Control
- Data Aggregation
- Data Analytics
- Data at rest
- Data Collection
- Data Confidentiality
- data consumer
- Data Description
- Data Discovery
- Data Economy
- Data Integrity
- Data Isolation
- Data lifecycle management
- Data Location
- Data Markets
- data owner
- Data Ownership
- Data Processing
- Data Protection
- data provider
- Data Publishing
- Data Quality
- data security
- Data Sovereignty
- Data Storage
- Data Transfer Project
- data transfer project anno
- Data Transfer Project Architecture
- Data Transfer Project Overview and Fundamentals
- Data Transfer Project Whitepaper
- Data Usage Control
- Data Visualisation and User Interaction
- Decision maker
- developer
- Device Authentication
- Device Security
- DIN 77005-1:2018-09
- DIN EN 50129
- DIN EN 50155
- DIN EN 61511
- DMA
- DMA Architecture
- DMA Service Technology Specification and Development Roadmap
- DTP Deployment
- DTP Ecosystem
- DTP Security & Privacy
- DTP System
- Dynamic Adjustability
- Dynamic Discovery
- Edge Analytics
- Edge computing
- Edgecross Architecture
- Edgecross Consortium
- Edgecross Consortium to Address Edge Integration in IIoT-enabled Architectures
- edgecross edge computing layer anno
- Edgecross Edgecomputing Layer
- Edgecross FA
- edgecross facility layer anno
- Edgecross IT Systems Layer
- edgecross it systems layer anno
- edgecross layer anno
- Edgecross Whitepaper
- end user
- Endpoint Description
- Endpoint Invocation
- Energy Control
- Energy Efficiency
- Event-Driven Messaging
- Evolvability
- Execution Variability
- Extensibility
- f i w a r e anno
- Fairness
- Fault Tolerance
- FIWARE
- fiware advanced ui anno
- FIWARE Advanced Web-based User Interface
- FIWARE Applications Services and Data Delivery
- fiware applications services and data delivery anno
- FIWARE Architecture
- fiware chapter anno
- FIWARE Cloud Hosting
- fiware cloud hosting anno
- fiware data context management anno
- FIWARE Data/Context Management
- FIWARE Interface to Networks and Devices
- FIWARE IoT Services Enablement
- fiware iot services enablement anno
- FIWARE Security
- fiware security anno
- Geo tracking
- Geospatial data and information
- governance
- Greening of IoT
- HTTP/1.1
- HTTP/2
- HTTPS
- i d s r a m business layer anno
- i d s r a m certification anno
- i d s r a m functional layer anno
- i d s r a m governance anno
- i d s r a m information layer anno
- i d s r a m layer anno
- i d s r a m process layer anno
- i d s r a m security anno
- i d s r a m system layer anno
- i d4me
- i e c 29115
- i e c 61508
- i e c 61511
- i e c 61804 p3
- i e c 61804 p4
- i e c 61804 p5
- i e c 61804 p6
- i e c 62264 p6
- i e c 62541
- i i c f framework layer anno
- i i c f link layer anno
- i i c f network layer anno
- i i c f physical layer anno
- i i c f tansport layer anno
- i i r a application domain anno
- i i r a business domain anno
- i i r a business viewpoint anno
- i i r a connectivity anno
- i i r a control domain anno
- i i r a crosscutting function anno
- i i r a functional viewpoint anno
- i i r a implementation viewpoint anno
- i i r a industrial analytics
- i i r a information domain anno
- i i r a operations domain anno
- i i r a reliability anno
- i i r a resilience anno
- i i r a safety anno
- i i r a security anno
- i i r a security framework anno
- i i r a usage viewpoint anno
- i s o 13485
- i s o 13849
- i s o 19941
- i s o 20140 p1
- Identification
- Identity Management
- IDS Data Market
- IDS Interoperability
- IDS RAM
- IDS RAM Business Layer
- IDS RAM Certification Perspective
- IDS RAM Functional Layer
- IDS RAM Governance Perspective
- IDS RAM Information Layer
- IDS RAM Process Layer
- IDS RAM Security Perspective
- IDS RAM System Layer
- IDS REFERENCE ARCHITECTURE MODEL INDUSTRIAL DATA SPACE VERSION 2.0
- IDS Trusted Connector
- IDSA
- IIC
- IIC Security Framework
- IIC Vocabulary
- IICF
- IICF
- iicf connectivity layer anno
- IICF Framework Layer
- IICF Link Layer
- IICF Network Layer
- IICF Physical Layer
- IICF Transport Layer
- IIRA Application Domain
- IIRA Business Domain
- IIRA Business Viewpoint
- IIRA Connectivity
- IIRA Control Domain
- IIRA Distributed Data Management
- IIRA Functional Viewpoint
- IIRA Implementation Viewpoint
- IIRA Information Domain
- IIRA Intelligent and Resilient Control
- IIRA Operation Domain
- IIRA Physical Systems
- IIRA Privacy
- IIRA Reliability
- IIRA Resilience
- IIRA Safety
- IIRA Scalability
- IIRA Security
- IIRA Usage Viewpoint
- industrial data space
- Industrial Internet Architecture Version 1
- Industrial Internet Architecture Version 1
- Industrial Internet of Things Volume G4: Security Framework
- Industrial Internet Reference Architecture
- Industrial Value Chain Reference Architecture
- Industrial Value Chain Reference Architecture (IVRA)
- Industrial Value Chain Reference Architecture (IVRA)- Next
- Information Privacy
- Information Security
- Integrity Protection and Verification
- interface networks devices anno
- Interoperability
- Introduction of X-tee
- IoT
- IoT-A
- IoT-A Availability and Resilience
- IoT-A Deployment and Operation
- IoT-A Evolution and Interoperability
- IoT-A Functional Viewpoint
- IoT-A Information Viewpoint
- IoT-A Performance and Scalability
- IoT-A Reference Architecture
- IoT-A Trust Security and Privacy
- iota availability resilience anno
- iota deployment operation viewpoint anno
- iota evolution interoperability anno
- iota functional viewpoint anno
- iota information viewpoint anno
- iota performance scalability anno
- iota perspective anno
- iota reference architecture anno
- iota trust security privacy anno
- IoTivity
- IPSO
- IPSO App Framework
- IPv4 Support
- IPv6
- IPv6 Support
- iShare
- ISO 50001
- ISO 9000
- ISO/IEC 29115
- ISO/IEC 9594
- ISO/IEC 9594-8
- Isolation
- IVI
- IVI Activity Layer
- ivi activity layer anno
- IVI Activity View
- ivi activity view anno
- IVI Asset View
- ivi asset view anno
- IVI Business Layer
- ivi business layer anno
- IVI Management View
- ivi management view anno
- IVI Specification Layer
- ivi specification layer anno
- JMS
- JSON Web Token
- Jurisdictional Issues
- key rock
- LatencyReduction
- LDAP
- Lightweight M2M v1.0
- Local Data Confidentiality
- Logging
- Long Term Business Sustainability
- low power wi fi
- Machine Learning
- Maintenance Cost
- Message precedence
- Mobil Devices
- Muhammad Usman
- Multilateralism
- Multiple Identities
- Network performance
- network security
- Network Virtualization
- NGSI
- NGSI-LD API Operation
- NGSI-LD Architecture
- NGSI-LD Data Representation
- NGSI-LD Information Model
- Non-repudiation
- o f r a agility pillar anno
- o f r a autonomy pillar anno
- o f r a data analytics and control perspective anno
- o f r a deployment viewpoint anno
- o f r a functional viewpoint anno
- o f r a hierarchy pillar anno
- o f r a it business and cross fog applications perspective anno
- o f r a manageability perspective anno
- o f r a node view anno
- o f r a openness pillar anno
- o f r a performance perspective anno
- o f r a programmability pillar anno
- o f r a r a s pillar anno
- o f r a scalability pillar anno
- o f r a security perspective anno
- o f r a security pillar anno
- o f r a software view
- o f r a software view anno
- o f r a system view anno
- Objects Safety and Security
- ocean business viewpoint anno
- ocean marketplace viewpoint anno
- Ocean Protocol
- Ocean Protocol Business Viewpoint
- Ocean Protocol Foundation
- Ocean Protocol Marketplace Viewpoint
- Ocean Protocol System Viewpoint
- Ocean Protocol: A Decentralized Data Exchange Protocol to Unlock Data for Artificial Intelligence. Reference Marketplace Framework. Feb 2019
- Ocean Protocol: A Decentralized Data Exchange Protocol,powered by blockchain technology and a cryptotoken. Business Strategy. Oct 2017
- Ocean Protocol: A Decentralized Substrate for AI Data & Services . Technical Whitepaper. Apr 2019
- ocean system viewpoint anno
- OCF Core Framework
- ocf core framework anno
- OCF Data Models
- ocf data models anno
- OCF Framework
- ocf framework anno
- OCF L2 Connectivity
- ocf l2 connectivity anno
- OCF Networking
- ocf networking anno
- OCF Security
- ocf security anno
- ODRL
- OMG DDS
- Open Connectivity Foundation
- Open Mobile Alliance
- OpenAPI
- OpenFog Agility Pillar
- OpenFog Architecture Whitepaper
- OpenFog AutonomyPillar
- OpenFog Consortium
- OpenFog Data Analytics and Control Perspective
- OpenFog Deployment Viewpoint
- OpenFog Functional Viewpoint
- OpenFog Hierarchy Pillar
- OpenFog IT Business and Cross-fog Applications Perspective
- OpenFog Manageability Perspective
- OpenFog Node View
- OpenFog Opennes Pillar
- OpenFog Programmability Pillar
- OpenFog RAS Pillar
- OpenFog Reference Architecture
- OpenFog Reference Architecture for Fog Computing
- OpenFog Scalability Pillar
- OpenFog Security Perspective
- OpenFog Security Pillar
- OpenFog System Architecture View
- ORION Context Broker
- Performance
- Performance and Scale Perspective
- Periodic Communication
- Physical Connectivity
- Physical Web
- Platform Industry 4.0
- Privacy
- Product Liability
- Product Manager
- Programmability
- project manager
- Provenance Tracking
- Pseudonimity
- Quality of Service
- r a m i assetlayer anno
- r a m i body anno
- r a m i business layer anno
- r a m i communicationlayer anno
- r a m i connected world
- r a m i connected world anno
- r a m i control device anno
- r a m i enterprise anno
- r a m i field device
- r a m i field device anno
- r a m i functional layer anno
- r a m i header anno
- r a m i information layer anno
- r a m i integration layer anno
- r a m i product
- r a m i product anno
- r a m i station anno
- r d f
- Radio activity control
- RAMI Asset Layer
- RAMI Business Layer
- RAMI Communication Layer
- RAMI Functional Layer
- RAMI Information Layer
- RAMI Integration Layer
- RAML
- Reactive Streams
- Real Time Analytics
- Regulatory Compliance
- Reliability
- Resilience
- REST
- Return On Investment
- RFC 1122
- RFC 5246
- RFC 6750
- RFC 7252
- RFC 7642
- RFC 7643
- RFC 7644
- RFC 768
- RFC 793
- Risk Management
- Role Categorization
- ROLL
- RPMA
- Safety
- Scalability
- SCIM
- Secure Communication
- Security
- Security Configuration
- Selection of Service Provider
- Semantic Interoperability
- Sensing
- Service Access Control
- Service Choreography
- Service Composition
- Service Deployment
- Service Description
- Service Discovery
- Service Isolation
- Service level agreement
- Service life-cycle management
- Service Orchestration
- Service Recovery
- Service Selection
- Software Updates
- Spatial modeling
- Stream processing
- Syntactic Interoperability
- System Engineer
- System evolution
- system operator
- System Recovery
- The Industrial Internet of Things Volume G1: Reference Architecture IIC:PUB:G1:V1.80:20170131
- The Industrial Internet of Things Volume G5: Connectivity Framework
- Thing description
- Thing mobility
- Thing representation
- Time Synchronization
- Trusted Connector
- Trustworthiness
- Unicast
- Unreliable Network
- User Interaction
- User Preferences
- Vendor Lockin
- Virtual Entity
- x a c m l
- x road deployment view anno
- x road protocols interfaces anno
- x road system components anno
- x road technology matrix anno
- x-road
- X-Road Architecture Technical Specification Version: 1.0 18.09.2015 15 pages Doc. ID: ARC-G
- x-road Deplyoment View
- x-road Protocols and Interfaces
- x-road System Components
- x-road Technology Matrix
- x-Tee
Industry 4.0 Knowledge Graph: Description back to ToC
Classes and properties from existing ontologies are reused, e.g., PROV for describing provenance of entities, and FOAF for representing and linking documents. DCTERMS for document metadata, such as licenses and titles as well as the RAMI4.0 ontology for linking Standards with RAMI4.0 concepts.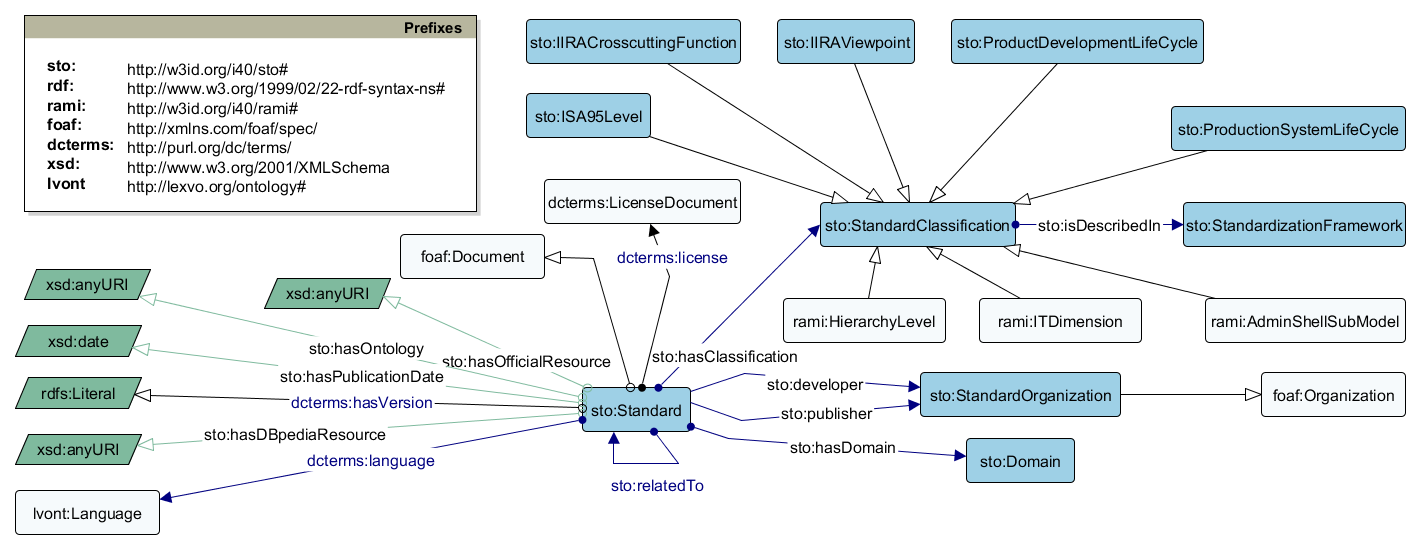
Cross reference for Industry 4.0 Knowledge Graph classes, properties and dataproperties back to ToC
This section provides details for each class and property defined by Industry 4.0 Knowledge Graph.Classes
- Admin Shell Sub Model
- Alliance of Industrial Internet Architecture Classification
- Architecture Description
- BDVA Concern
- Business Cycle SCM
- Connectivity Layer
- Connectivity Layer
- Data Sharing Initiative
- Domain
- Edgecross Layer
- Fiware Chapter
- i io t consortium
- IDS RAM Layer
- IDS RAM Layer
- IDS RAM Perspective
- IDS RAM Perspective
- IIRA Crosscutting Function
- IIRA Crosscutting Function
- IIRA Functional Domain
- IIRA Functional Domain
- IIRA System Characteristic
- IIRA System Characteristic
- IoT-A Perspective
- ISA 95 Level
- IVI Layer
- Layer
- Layer
- License Document
- NGSI Context Information Management API
- OCF Framework Block
- Product Development Life Cycle
- Production System Life Cycle
- RAMI Hierarchy Level
- RAMI IT Layer
- RAMI Life Cycle Layer RAMI Life Cycle Layer
- Standard
- Standard Classification
- StandardOrganization
- StandardPart
- Standarization Framework
- Technical Report
- Technical Specification
- Technology
- Viewpoint
- x-road Section
Admin Shell Sub Modelc back to ToC or Class ToC
IRI: https://w3id.org/i40/rami#AdminShellSubmodel
- has super-classes
- Standard Classification c
- has members
- Energy Efficiency ni, communication ni
Alliance of Industrial Internet Architecture Classificationc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#AiiClassification
- has super-classes
- Standard Classification c
- has members
- AII Data Classification ni, AII Network Classification ni, AII Security Classification ni
Architecture Descriptionc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#ArchitectureDescription
- has super-classes
- Standarization Framework c
- has members
- AII Industrial Internet Architecture ni, DMA Architecture ni, Data Transfer Project Architecture ni, Edgecross Architecture ni, FIWARE Architecture ni, IDS RAM ni, Industrial Internet Reference Architecture ni, Industrial Value Chain Reference Architecture ni, IoT-A Reference Architecture ni, OpenFog Reference Architecture ni, x-Tee ni
BDVA Concernc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#BdvaConcern
- has super-classes
- Standard Classification c
- has members
- BDVA Cloud and High Performance Computing ni, BDVA Communication and Connectivity ni, BDVA Cybersecurity and Trust ni, BDVA Data Analytics ni, BDVA Data Management ni, BDVA Data Processing Architectures ni, BDVA Data Protection ni, BDVA Data Sharing Platforms ni, BDVA Engineering and DevOps ni, BDVA IoT CPS and Edge Computing ni, BDVA Standards ni, Data Visualisation and User Interaction ni
- is also defined as
- named individual
Business Cycle SCMc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#BusinessCycleSCM
- has super-classes
- Standard Classification c
Connectivity Layerc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#ConnectivityLayer
- has super-classes
- Standard Classification c
Connectivity Layerc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#IicfConnectivityLayer
- has super-classes
- Standard Classification c
- has members
- IICF Framework Layer ni, IICF Link Layer ni, IICF Network Layer ni, IICF Physical Layer ni, IICF Transport Layer ni
- is also defined as
- named individual
Data Sharing Initiativec back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#DataSharingInitiative
- has super-classes
- organization c
- has members
- DMA ni, Data Transfer Project ni, x-road ni
- is also defined as
- named individual
Domainc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#Domain
- is in domain of
- has Domain Name dp
- is in range of
- has domain op
Edgecross Layerc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#EdgecrossLayer
- has super-classes
- Standard Classification c
- has members
- Edgecross Edgecomputing Layer ni, Edgecross FA ni, Edgecross IT Systems Layer ni
Fiware Chapterc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#FiwareChapter
- has super-classes
- Standard Classification c
- has members
- FIWARE Advanced Web-based User Interface ni, FIWARE Applications Services and Data Delivery ni, FIWARE Cloud Hosting ni, FIWARE Data/Context Management ni, FIWARE Interface to Networks and Devices ni, FIWARE IoT Services Enablement ni, FIWARE Security ni
- is also defined as
- named individual
i io t consortiumc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#IIoTConsortium
- has super-classes
- organization c
- has members
- AllSeen Alliance ni, Alliance Industrie du Futur ni, Alliance of Industrial Internet ni, Arrowhead Framework ni, Edgecross Consortium ni, IDSA ni, IIC ni, IPSO ni, IVI ni, IoT-A ni, Open Mobile Alliance ni, OpenFog Consortium ni, Platform Industry 4.0 ni
IDS RAM Layerc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#IDSRAMLayer
- is equivalent to
- { IDS RAM Business Layer , IDS RAM Functional Layer , IDS RAM Information Layer , IDS RAM Process Layer , IDS RAM System Layer }
- has super-classes
- Standard Classification c
- has members
- IDS RAM Business Layer ni, IDS RAM Functional Layer ni, IDS RAM Information Layer ni, IDS RAM Process Layer ni, IDS RAM System Layer ni
IDS RAM Layerc back to ToC or Class ToC
IRI: https://w3id.org/ids/ram/Layer
- is equivalent to
- { business layer , functional layer , information layer , process layer , system layer }
- has super-classes
- Standard Classification c
IDS RAM Perspectivec back to ToC or Class ToC
IRI: http://w3id.org/ids/ram/Perspective
- is equivalent to
- { certification , governance , security }
- has super-classes
- Standard Classification c
IDS RAM Perspectivec back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#IdsPerspective
- is equivalent to
- { IDS RAM Certification Perspective , IDS RAM Governance Perspective , IDS RAM Security Perspective }
- has super-classes
- Standard Classification c
- has members
- IDS RAM Certification Perspective ni, IDS RAM Governance Perspective ni, IDS RAM Security Perspective ni
- is also defined as
- named individual
IIRA Crosscutting Functionc back to ToC or Class ToC
IRI: http://example.org/iira#CrosscuttingFunction
- has super-classes
- Standard Classification c
IIRA Crosscutting Functionc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#IIRACrosscuttingFunction
- has super-classes
- Standard Classification c
- has members
- IIRA Connectivity ni, IIRA Distributed Data Management ni, IIRA Intelligent and Resilient Control ni, i i r a industrial analytics ni
- is also defined as
- named individual
IIRA Functional Domainc back to ToC or Class ToC
IRI: http://example.org/iira#FunctionalDomain
- has super-classes
- Standard Classification c
IIRA Functional Domainc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#IIRAFunctionalDomain
- has super-classes
- Standard Classification c
- has members
- IIRA Application Domain ni, IIRA Business Domain ni, IIRA Control Domain ni, IIRA Information Domain ni, IIRA Operation Domain ni
- is also defined as
- named individual
IIRA System Characteristicc back to ToC or Class ToC
IRI: http://example.org/iira#SystemCharacteristics
- has super-classes
- Standard Classification c
IIRA System Characteristicc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#IIRASystemCharacteristics
- has super-classes
- Standard Classification c
- has members
- IIRA Privacy ni, IIRA Reliability ni, IIRA Resilience ni, IIRA Safety ni, IIRA Scalability ni, IIRA Security ni
- is also defined as
- named individual
IoT-A Perspectivec back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#IotaPerspective
- has super-classes
- Standard Classification c
- has members
- IoT-A Availability and Resilience ni, IoT-A Evolution and Interoperability ni, IoT-A Performance and Scalability ni, IoT-A Trust Security and Privacy ni
- is also defined as
- named individual
ISA 95 Levelc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#ISA95Level
- has super-classes
- Standard Classification c
- is in domain of
- has Objective dp, has Task dp
IVI Layerc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#IviLayer
- has super-classes
- Standard Classification c
- has members
- IVI Activity Layer ni, IVI Business Layer ni, IVI Specification Layer ni
Layerc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#Layer
Layerc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#Stakeholder
- has super-classes
- person c
- has members
- Decision maker ni, Product Manager ni, System Engineer ni
License Documentc back to ToC or Class ToC
IRI: http://purl.org/dc/terms/LicenseDocument
- Is defined by
- http://purl.org/dc/terms/
NGSI Context Information Management APIc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#NGSI_Context_Information_Management_API
- has super-classes
- Standard Classification c
- has members
- NGSI-LD API Operation ni, NGSI-LD Architecture ni, NGSI-LD Data Representation ni, NGSI-LD Information Model ni
OCF Framework Blockc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#OcfBlock
- has super-classes
- Standard Classification c
- has members
- OCF Core Framework ni, OCF Data Models ni, OCF L2 Connectivity ni, OCF Networking ni, OCF Security ni
Product Development Life Cyclec back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#ProductDevelopmentLifeCycle
- Is defined by
- https://w3id.org/i40/sto
- has super-classes
- Standard Classification c
Production System Life Cyclec back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#ProductionSystemLifeCycle
- has super-classes
- Standard Classification c
RAMI Hierarchy Levelc back to ToC or Class ToC
IRI: https://w3id.org/i40/rami#RAMIHierarchyLevel
- is equivalent to
- { connected world , control device , enterprise , field device , product , station , work center }
- has super-classes
- Standard Classification c
- has members
- r a m i connected world ni, r a m i field device ni, r a m i product ni
RAMI IT Layerc back to ToC or Class ToC
IRI: https://w3id.org/i40/rami#RAMIITLayer
- is equivalent to
- { asset , business , communication , functional , information , integration }
- has super-classes
- Standard Classification c
- has members
- RAMI Asset Layer ni, RAMI Business Layer ni, RAMI Communication Layer ni, RAMI Functional Layer ni, RAMI Information Layer ni, RAMI Integration Layer ni
RAMI Life Cycle Layerc back to ToC or Class ToC
RAMI Life Cycle Layerc back to ToC or Class ToC
IRI: https://w3id.org/i40/rami#RAMILifeCycleLayer
- has super-classes
- Standard Classification c
Standardc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#Standard
- has super-classes
- Publication
- is in domain of
- has Classification op, has Target Concern op, is Component Of op, related To op
- is in range of
- related To op
- has members
- DIN 77005-1:2018-09 ni, DIN EN 50129 ni, DIN EN 50155 ni, DIN EN 61511 ni, HTTP/1.1 ni, HTTP/2 ni, HTTPS ni, ISO 50001 ni, ISO 9000 ni, ISO/IEC 29115 ni, ISO/IEC 9594 ni, ISO/IEC 9594-8 ni, JSON Web Token ni, ODRL ni, OMG DDS ni, RFC 1122 ni, RFC 5246 ni, RFC 6750 ni, RFC 7252 ni, RFC 7642 ni, RFC 7643 ni, RFC 7644 ni, RFC 768 ni, RFC 793 ni, d i n e n 50128 ni, d i n e n 50159 ni, d i n e n i s o 13849 ni, d i n e n i s o i e c 17025 ni, d i n i s o 14638 ni, d i n s p e c 16593 p1 ni, d i n s p e c 92222 ni, i e c 29115 ni, i e c 61508 ni, i e c 61511 ni, i e c 61804 p3 ni, i e c 61804 p4 ni, i e c 61804 p5 ni, i e c 62264 p6 ni, i e c 62541 ni, i s o 13485 ni, i s o 13849 ni, i s o 19941 ni, i s o 20140 p1 ni
Standard Classificationc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#StandardClassification
- has sub-classes
- Admin Shell Sub Model c, Alliance of Industrial Internet Architecture Classification c, BDVA Concern c, Business Cycle SCM c, Connectivity Layer c, Connectivity Layer c, Edgecross Layer c, Fiware Chapter c, IDS RAM Layer c, IDS RAM Layer c, IDS RAM Perspective c, IDS RAM Perspective c, IIRA Crosscutting Function c, IIRA Crosscutting Function c, IIRA Functional Domain c, IIRA Functional Domain c, IIRA System Characteristic c, IIRA System Characteristic c, ISA 95 Level c, IVI Layer c, IoT-A Perspective c, NGSI Context Information Management API c, OCF Framework Block c, Product Development Life Cycle c, Production System Life Cycle c, RAMI Hierarchy Level c, RAMI IT Layer c, RAMI Life Cycle Layer RAMI Life Cycle Layer c, Viewpoint c, x-road Section c
- is in domain of
- alignes With op, alignes With op, frames op, is Described in op
- is in range of
- alignes With op, alignes With op, has Classification op
- has members
- Administration Shell ni, Administration Shell Header ni, BDVA Cloud and High Performance Computing ni, BDVA Communication and Connectivity ni, BDVA Cybersecurity and Trust ni, BDVA Data Analytics ni, BDVA Data Management ni, BDVA Data Processing Architectures ni, BDVA Data Protection ni, BDVA Data Sharing Platforms ni, BDVA Engineering and DevOps ni, BDVA IoT CPS and Edge Computing ni, BDVA Standards ni, DTP Deployment ni, DTP Ecosystem ni, DTP Security & Privacy ni, DTP System ni, Data Sovereignty ni, Data Visualisation and User Interaction ni, Edgecross Edgecomputing Layer ni, Edgecross FA ni, Edgecross IT Systems Layer ni, Energy Efficiency ni, FIWARE Advanced Web-based User Interface ni, FIWARE Applications Services and Data Delivery ni, FIWARE Cloud Hosting ni, FIWARE Data/Context Management ni, FIWARE Interface to Networks and Devices ni, FIWARE IoT Services Enablement ni, FIWARE Security ni, IDS Data Market ni, IDS Interoperability ni, IDS RAM Business Layer ni, IDS RAM Certification Perspective ni, IDS RAM Functional Layer ni, IDS RAM Governance Perspective ni, IDS RAM Information Layer ni, IDS RAM Process Layer ni, IDS RAM Security Perspective ni, IDS RAM System Layer ni, IIC Security Framework ni, IIC Vocabulary ni, IICF Framework Layer ni, IICF Link Layer ni, IICF Network Layer ni, IICF Physical Layer ni, IICF Transport Layer ni, IIRA Application Domain ni, IIRA Business Domain ni, IIRA Business Viewpoint ni, IIRA Connectivity ni, IIRA Control Domain ni, IIRA Distributed Data Management ni, IIRA Functional Viewpoint ni, IIRA Implementation Viewpoint ni, IIRA Information Domain ni, IIRA Intelligent and Resilient Control ni, IIRA Operation Domain ni, IIRA Physical Systems ni, IIRA Privacy ni, IIRA Reliability ni, IIRA Resilience ni, IIRA Safety ni, IIRA Scalability ni, IIRA Security ni, IIRA Usage Viewpoint ni, IVI Activity Layer ni, IVI Activity View ni, IVI Asset View ni, IVI Business Layer ni, IVI Management View ni, IVI Specification Layer ni, Identification ni, IoT-A Availability and Resilience ni, IoT-A Deployment and Operation ni, IoT-A Evolution and Interoperability ni, IoT-A Functional Viewpoint ni, IoT-A Information Viewpoint ni, IoT-A Performance and Scalability ni, IoT-A Trust Security and Privacy ni, NGSI-LD API Operation ni, NGSI-LD Architecture ni, NGSI-LD Data Representation ni, NGSI-LD Information Model ni, Ocean Protocol Business Viewpoint ni, Ocean Protocol Marketplace Viewpoint ni, Ocean Protocol System Viewpoint ni, OpenFog Agility Pillar ni, OpenFog AutonomyPillar ni, OpenFog Data Analytics and Control Perspective ni, OpenFog Hierarchy Pillar ni, OpenFog IT Business and Cross-fog Applications Perspective ni, OpenFog Manageability Perspective ni, OpenFog Opennes Pillar ni, OpenFog Programmability Pillar ni, OpenFog RAS Pillar ni, OpenFog Scalability Pillar ni, OpenFog Security Perspective ni, OpenFog Security Pillar ni, Performance and Scale Perspective ni, RAMI Asset Layer ni, RAMI Business Layer ni, RAMI Communication Layer ni, RAMI Functional Layer ni, RAMI Information Layer ni, RAMI Integration Layer ni, communication ni, i i r a industrial analytics ni, r a m i field device ni, r a m i product ni, x-road Deplyoment View ni, x-road Protocols and Interfaces ni, x-road System Components ni, x-road Technology Matrix ni
StandardOrganizationc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#StandardOrganization
- has super-classes
- organization c
- is in domain of
- Org Name dp, belongs To op, has Formation Date dp, has Headquater In op
- is in range of
- has Developer op, has Publisher op
- has members
- DMA ni, Edgecross Consortium ni, IIC ni, Ocean Protocol Foundation ni, Open Connectivity Foundation ni
StandardPartc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#StandardPart
- has super-classes
- Publication
- is in domain of
- std Part Name dp
Standarization Frameworkc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#StandardizationFramework
- has sub-classes
- Architecture Description c
- is in range of
- is Described in op
- has members
- Administration Shell ni, Administration Shell Header ni, Arrowhead Framework ni, BDVA SIRA ni, DMA Architecture ni, DMA Service Technology Specification and Development Roadmap ni, Data Transfer Project Architecture ni, Edgecross Architecture ni, FIWARE Architecture ni, IDS RAM ni, IICF ni, Industrial Internet Reference Architecture ni, Industrial Value Chain Reference Architecture ni, IoT-A Reference Architecture ni, OCF Framework ni, Ocean Protocol ni, OpenFog Reference Architecture ni, industrial data space ni, x-Tee ni
Technical Reportc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#TechnicalReport
- has super-classes
- Publication
- has members
- Introduction of X-tee ni, i e c 61804 p6 ni
Technical Specificationc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#TechnicalSpecification
- has super-classes
- Publication
- has members
- 6LoWPAN ni, AMQP ni, Aeron ni, Alljoyn ni, Blockchain ni, Bluetooth ni, CoAP ni, IPSO App Framework ni, IPv6 ni, IoTivity ni, JMS ni, LDAP ni, Lightweight M2M v1.0 ni, NGSI ni, ORION Context Broker ni, Ocean Protocol ni, OpenAPI ni, Physical Web ni, RAML ni, REST ni, ROLL ni, RPMA ni, Reactive Streams ni, SCIM ni, i d4me ni, key rock ni, low power wi fi ni, r d f ni, x a c m l ni
Technologyc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#Technology
- has members
- IDS Trusted Connector ni, Trusted Connector ni
Viewpointc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#Viewpoint
- has super-classes
- Standard Classification c
- is in domain of
- frames op
- has members
- DTP Deployment ni, DTP Ecosystem ni, DTP Security & Privacy ni, DTP System ni, IIRA Business Viewpoint ni, IIRA Functional Viewpoint ni, IIRA Implementation Viewpoint ni, IIRA Usage Viewpoint ni, IVI Activity View ni, IVI Asset View ni, IVI Management View ni, IoT-A Deployment and Operation ni, IoT-A Functional Viewpoint ni, IoT-A Information Viewpoint ni, Ocean Protocol Business Viewpoint ni, Ocean Protocol Marketplace Viewpoint ni, Ocean Protocol System Viewpoint ni, OpenFog Deployment Viewpoint ni, OpenFog Functional Viewpoint ni, OpenFog Node View ni, OpenFog System Architecture View ni, o f r a software view ni
x-road Sectionc back to ToC or Class ToC
IRI: https://w3id.org/i40/sto#xRoadSection
- has super-classes
- Standard Classification c
- has members
- x-road Deplyoment View ni, x-road Protocols and Interfaces ni, x-road System Components ni, x-road Technology Matrix ni
Object Properties
- alignes With
- alignes With
- belongs To
- frames
- frames
- has Available Language
- has Classification
- has Developer
- has domain
- has File Size
- has Headquater In
- has ICS
- has motivation
- has Previous Version
- has Publisher
- has Target Concern
- has Target Concern
- has Technical Committee
- has unit
- is Component Of
- is Described in
- is Implementation Of
- is member of
- related To
- supports
- use Structure Of
- uses
- was Generated By
alignes Withop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#alignesWith
has characteristics: symmetric
- has super-properties
- associated with op
- has domain
- Standard Classification c
- has range
- Standard Classification c
alignes Withop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto/iot#alignsWith
has characteristics: symmetric
- has super-properties
- associated with op
- has domain
- Standard Classification c
- has range
- Standard Classification c
- is inverse of
- alignes With op, alignes With op
belongs Toop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#belongsTo
- has domain
- StandardOrganization c
- has range
- country c
framesop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#frames
- has super-properties
- associated with op
- has domain
- Viewpoint c
- has range
- Concern c
framesop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto/iot#frames
- has super-properties
- associated with op
- has domain
- Standard Classification c
- has range
- Concern c
has Available Languageop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasAvailableLanguage
- has super-properties
- language op
- has domain
- document c
- has range
- linguistic system c
has Classificationop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasClassification
- has domain
- Standard c
- has range
- Standard Classification c
has Developerop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasDeveloper
- has super-properties
- maker op
- has domain
- Publication
- has range
- StandardOrganization c
has domainop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasDomain
- has domain
- Publication
- has range
- Domain c
has File Sizeop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasFileSize
- has domain
- document c
- has range
- measure c
has Headquater Inop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasHeadquaterIn
- has domain
- StandardOrganization c
- has range
- place c
has ICSop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasICS
- has domain
- Publication
- has range
- international classification for standards
has motivationop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasMotivation
- has domain
- Publication
- has range
- motivation c
has Previous Versionop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasPreviousVersion
- has super-properties
- related To op
has Publisherop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasPublisher
- has super-properties
- maker op
- has domain
- Publication
- has range
- StandardOrganization c
has Target Concernop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasTargetConcern
- has super-properties
- associated with op
- has domain
- Standard c
- has range
- Concern c
has Target Concernop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto/iot#hasTargetConcern
- has super-properties
- associated with op
- has domain
- Standard c or Standarization Framework c
- is also defined as
- annotation property
has Technical Committeeop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#hasTechnicalCommittee
- has domain
- Publication
- has range
- technical committee
has unitop back to ToC or Object Property ToC
IRI: http://www.ontology-of-units-of-measure.org/resource/om-2/hasUnit
- has domain
- error1 c
- has range
- unit
is Component Ofop back to ToC or Object Property ToC
IRI: http://www.ontologydesignpatterns.org/ont/dul/DUL.owl#isComponentOf
- Is defined by
- http://www.ontologydesignpatterns.org/ont/dul/DUL.owl
- has super-properties
- related To op
- has domain
- Standard c
- has range
- Standard c or StandardPart c
is Described inop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#isDescribedin
- has domain
- Standard Classification c
- has range
- Standarization Framework c
is Implementation Ofop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#isImplementationOf
- has super-properties
- related To op
is member ofop back to ToC or Object Property ToC
IRI: http://www.ontologydesignpatterns.org/ont/dul/DUL.owl#isMemberOf
- Is defined by
- http://www.ontologydesignpatterns.org/ont/dul/DUL.owl
- has super-properties
- associated with op
- has domain
- entity
- has range
- collection
supportsop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto/iot#supports
- has domain
- Concern c
- has range
- Concern c
use Structure Ofop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#useStructureOf
- has super-properties
- related To op
usesop back to ToC or Object Property ToC
IRI: https://w3id.org/i40/sto#uses
- has super-properties
- related To op
was Generated Byop back to ToC or Object Property ToC
IRI: http://www.w3.org/ns/prov#wasGeneratedBy
- Is defined by
- https://w3id.org/i40/sto
- has super-properties
- related To op
Data Properties
- has Abbreviated Name
- has Domain Name
- has Edition
- has Formation Date
- has Implementation Format
- has numerical value
- has Objective
- has official resource
- has Ontology
- has Pages
- has Publication Date
- has Stability Date
- has Status
- has tag
- has Task
- Org Name
- std Part Name
has Abbreviated Namedp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#abbreviation
- has domain
- thing c
- has range
- plain literal
has Domain Namedp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#domainName
- has domain
- Domain c
- has range
- plain literal
has Editiondp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasEdition
- has domain
- document c
- has range
- float
has Formation Datedp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#formationDate
has characteristics: functional
- has domain
- StandardOrganization c
- has range
- date
has Implementation Formatdp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasImplementationFormat
- has domain
- Publication
- has range
- literal
has numerical valuedp back to ToC or Data Property ToC
IRI: http://www.ontology-of-units-of-measure.org/resource/om-2/hasNumericalValue
- has domain
- _:genid-nodeid-genid-ac8058d3efd24203949d2f943abb9621-6780A905CC831CAB4C4E310C38E6329A c
has Objectivedp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasObjective
- has domain
- ISA 95 Level c
- has range
- string
has official resourcedp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasOfficialResource
- has domain
- Publication
- has range
- any u r i
has Ontologydp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasOntology
- has domain
- Publication
- has range
- any u r i
has Pagesdp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasPages
- has domain
- document c
- has range
- integer
has Publication Datedp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasPublicationDate
- has domain
- Publication
- has range
- date
has Stability Datedp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasStabilityDate
- has domain
- Publication
- has range
- g year
has Statusdp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasStatus
- has domain
- Publication
- has range
- literal
has tagdp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasTag
- has range
- tag
- literal
has Taskdp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#hasTask
- has domain
- ISA 95 Level c
- has range
- string
Org Namedp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#orgName
- has domain
- StandardOrganization c
- has range
- plain literal
std Part Namedp back to ToC or Data Property ToC
IRI: https://w3id.org/i40/sto#stoPartName
- has domain
- StandardPart c
- has range
- string
Named Individuals
- 6LoWPAN
- Access Policy
- Access Rights for IoT-Cloud
- Accountability
- Actuation
- Adaptability
- Administration Shell
- Administration Shell Header
- Aeron
- agility
- aii data anno
- AII Data Classification
- AII Industrial Internet Architecture
- aii network anno
- AII Network Classification
- aii security anno
- AII Security Classification
- Alliance Industrie du Futur
- Alliance of Industrial Internet
- Alljoyn
- AllSeen Alliance
- AMQP
- anno actuation
- anno aii classification
- Anonymity
- Arrowhead Framework
- Arrowhead Project
- Artificial Intelligence
- Asset Management
- Authentication
- authorization
- Auto Scaling
- Autonomous Communication
- Autonomous Configuration
- Availability
- Awareness
- Bandwidth
- BDV SRIA European Big Data Value Strategic Research and Innovation Agenda version 4.0 October 2017
- BDVA Cloud and High Performance Computing
- bdva cloud and high performance computing anno
- BDVA Communication and Connectivity
- bdva communication connectivity anno
- BDVA Concern
- bdva concern anno
- bdva cyber security trust anno
- BDVA Cybersecurity and Trust
- BDVA Data Analytics
- bdva data analytics anno
- BDVA Data Management
- bdva data management anno
- BDVA Data Processing Architectures
- bdva data processing architectures anno
- BDVA Data Protection
- bdva data protection anno
- BDVA Data Sharing Platforms
- bdva data sharing platforms anno
- bdva data visualization and user interaction anno
- bdva development engineering anno
- BDVA Engineering and DevOps
- BDVA IoT CPS and Edge Computing
- BDVA SIRA
- bdva sira anno
- BDVA Standards
- bdva standards anno
- bdva things assets sensors actuators anno
- Big Data Applications
- Big Data Value Association
- Blockchain
- Bluetooth
- BPM
- Business Context
- Business Transactions
- Business Value
- cardinality of data sources
- Cardinality of Participants
- CEP
- Certification
- Cloud Computing Capability
- cloud connectivity
- CoAP
- communication
- Compliance
- Confidentiality
- Connectivity
- Constrained Devices
- Context Awareness
- Cost Efficiency
- Cross-domain Identity Management
- customer
- Customization
- Customization
- d i n e n 50128
- d i n e n 50159
- d i n e n i s o 13849
- d i n e n i s o i e c 17025
- d i n i s o 14638
- d i n s p e c 16593 p1
- d i n s p e c 92222
- Data Access
- Data Access Control
- Data Aggregation
- Data Analytics
- Data at rest
- Data Collection
- Data Confidentiality
- data consumer
- Data Description
- Data Discovery
- Data Economy
- Data Integrity
- Data Isolation
- Data lifecycle management
- Data Location
- Data Markets
- data owner
- Data Ownership
- Data Processing
- Data Protection
- data provider
- Data Publishing
- Data Quality
- data security
- Data Sovereignty
- Data Storage
- Data Transfer Project
- data transfer project anno
- Data Transfer Project Architecture
- Data Transfer Project Overview and Fundamentals
- Data Transfer Project Whitepaper
- Data Usage Control
- Data Visualisation and User Interaction
- Decision maker
- developer
- Device Authentication
- Device Security
- DIN 77005-1:2018-09
- DIN EN 50129
- DIN EN 50155
- DIN EN 61511
- DMA
- DMA Architecture
- DMA Service Technology Specification and Development Roadmap
- DTP Deployment
- DTP Ecosystem
- DTP Security & Privacy
- DTP System
- Dynamic Adjustability
- Dynamic Discovery
- Edge Analytics
- Edge computing
- Edgecross Architecture
- Edgecross Consortium
- Edgecross Consortium to Address Edge Integration in IIoT-enabled Architectures
- edgecross edge computing layer anno
- Edgecross Edgecomputing Layer
- Edgecross FA
- edgecross facility layer anno
- Edgecross IT Systems Layer
- edgecross it systems layer anno
- edgecross layer anno
- Edgecross Whitepaper
- end user
- Endpoint Description
- Endpoint Invocation
- Energy Control
- Energy Efficiency
- Event-Driven Messaging
- Evolvability
- Execution Variability
- Extensibility
- f i w a r e anno
- Fairness
- Fault Tolerance
- FIWARE
- fiware advanced ui anno
- FIWARE Advanced Web-based User Interface
- FIWARE Applications Services and Data Delivery
- fiware applications services and data delivery anno
- FIWARE Architecture
- fiware chapter anno
- FIWARE Cloud Hosting
- fiware cloud hosting anno
- fiware data context management anno
- FIWARE Data/Context Management
- FIWARE Interface to Networks and Devices
- FIWARE IoT Services Enablement
- fiware iot services enablement anno
- FIWARE Security
- fiware security anno
- Geo tracking
- Geospatial data and information
- governance
- Greening of IoT
- HTTP/1.1
- HTTP/2
- HTTPS
- i d s r a m business layer anno
- i d s r a m certification anno
- i d s r a m functional layer anno
- i d s r a m governance anno
- i d s r a m information layer anno
- i d s r a m layer anno
- i d s r a m process layer anno
- i d s r a m security anno
- i d s r a m system layer anno
- i d4me
- i e c 29115
- i e c 61508
- i e c 61511
- i e c 61804 p3
- i e c 61804 p4
- i e c 61804 p5
- i e c 61804 p6
- i e c 62264 p6
- i e c 62541
- i i c f framework layer anno
- i i c f link layer anno
- i i c f network layer anno
- i i c f physical layer anno
- i i c f tansport layer anno
- i i r a application domain anno
- i i r a business domain anno
- i i r a business viewpoint anno
- i i r a connectivity anno
- i i r a control domain anno
- i i r a crosscutting function anno
- i i r a functional viewpoint anno
- i i r a implementation viewpoint anno
- i i r a industrial analytics
- i i r a information domain anno
- i i r a operations domain anno
- i i r a reliability anno
- i i r a resilience anno
- i i r a safety anno
- i i r a security anno
- i i r a security framework anno
- i i r a usage viewpoint anno
- i s o 13485
- i s o 13849
- i s o 19941
- i s o 20140 p1
- Identification
- Identity Management
- IDS Data Market
- IDS Interoperability
- IDS RAM
- IDS RAM Business Layer
- IDS RAM Certification Perspective
- IDS RAM Functional Layer
- IDS RAM Governance Perspective
- IDS RAM Information Layer
- IDS RAM Process Layer
- IDS RAM Security Perspective
- IDS RAM System Layer
- IDS REFERENCE ARCHITECTURE MODEL INDUSTRIAL DATA SPACE VERSION 2.0
- IDS Trusted Connector
- IDSA
- IIC
- IIC Security Framework
- IIC Vocabulary
- IICF
- IICF
- iicf connectivity layer anno
- IICF Framework Layer
- IICF Link Layer
- IICF Network Layer
- IICF Physical Layer
- IICF Transport Layer
- IIRA Application Domain
- IIRA Business Domain
- IIRA Business Viewpoint
- IIRA Connectivity
- IIRA Control Domain
- IIRA Distributed Data Management
- IIRA Functional Viewpoint
- IIRA Implementation Viewpoint
- IIRA Information Domain
- IIRA Intelligent and Resilient Control
- IIRA Operation Domain
- IIRA Physical Systems
- IIRA Privacy
- IIRA Reliability
- IIRA Resilience
- IIRA Safety
- IIRA Scalability
- IIRA Security
- IIRA Usage Viewpoint
- industrial data space
- Industrial Internet Architecture Version 1
- Industrial Internet Architecture Version 1
- Industrial Internet of Things Volume G4: Security Framework
- Industrial Internet Reference Architecture
- Industrial Value Chain Reference Architecture
- Industrial Value Chain Reference Architecture (IVRA)
- Industrial Value Chain Reference Architecture (IVRA)- Next
- Information Privacy
- Information Security
- Integrity Protection and Verification
- interface networks devices anno
- Interoperability
- Introduction of X-tee
- IoT
- IoT-A
- IoT-A Availability and Resilience
- IoT-A Deployment and Operation
- IoT-A Evolution and Interoperability
- IoT-A Functional Viewpoint
- IoT-A Information Viewpoint
- IoT-A Performance and Scalability
- IoT-A Reference Architecture
- IoT-A Trust Security and Privacy
- iota availability resilience anno
- iota deployment operation viewpoint anno
- iota evolution interoperability anno
- iota functional viewpoint anno
- iota information viewpoint anno
- iota performance scalability anno
- iota perspective anno
- iota reference architecture anno
- iota trust security privacy anno
- IoTivity
- IPSO
- IPSO App Framework
- IPv4 Support
- IPv6
- IPv6 Support
- iShare
- ISO 50001
- ISO 9000
- ISO/IEC 29115
- ISO/IEC 9594
- ISO/IEC 9594-8
- Isolation
- IVI
- IVI Activity Layer
- ivi activity layer anno
- IVI Activity View
- ivi activity view anno
- IVI Asset View
- ivi asset view anno
- IVI Business Layer
- ivi business layer anno
- IVI Management View
- ivi management view anno
- IVI Specification Layer
- ivi specification layer anno
- JMS
- JSON Web Token
- Jurisdictional Issues
- key rock
- LatencyReduction
- LDAP
- Lightweight M2M v1.0
- Local Data Confidentiality
- Logging
- Long Term Business Sustainability
- low power wi fi
- Machine Learning
- Maintenance Cost
- Message precedence
- Mobil Devices
- Muhammad Usman
- Multilateralism
- Multiple Identities
- Network performance
- network security
- Network Virtualization
- NGSI
- NGSI-LD API Operation
- NGSI-LD Architecture
- NGSI-LD Data Representation
- NGSI-LD Information Model
- Non-repudiation
- o f r a agility pillar anno
- o f r a autonomy pillar anno
- o f r a data analytics and control perspective anno
- o f r a deployment viewpoint anno
- o f r a functional viewpoint anno
- o f r a hierarchy pillar anno
- o f r a it business and cross fog applications perspective anno
- o f r a manageability perspective anno
- o f r a node view anno
- o f r a openness pillar anno
- o f r a performance perspective anno
- o f r a programmability pillar anno
- o f r a r a s pillar anno
- o f r a scalability pillar anno
- o f r a security perspective anno
- o f r a security pillar anno
- o f r a software view
- o f r a software view anno
- o f r a system view anno
- Objects Safety and Security
- ocean business viewpoint anno
- ocean marketplace viewpoint anno
- Ocean Protocol
- Ocean Protocol Business Viewpoint
- Ocean Protocol Foundation
- Ocean Protocol Marketplace Viewpoint
- Ocean Protocol System Viewpoint
- Ocean Protocol: A Decentralized Data Exchange Protocol to Unlock Data for Artificial Intelligence. Reference Marketplace Framework. Feb 2019
- Ocean Protocol: A Decentralized Data Exchange Protocol,powered by blockchain technology and a cryptotoken. Business Strategy. Oct 2017
- Ocean Protocol: A Decentralized Substrate for AI Data & Services . Technical Whitepaper. Apr 2019
- ocean system viewpoint anno
- OCF Core Framework
- ocf core framework anno
- OCF Data Models
- ocf data models anno
- OCF Framework
- ocf framework anno
- OCF L2 Connectivity
- ocf l2 connectivity anno
- OCF Networking
- ocf networking anno
- OCF Security
- ocf security anno
- ODRL
- OMG DDS
- Open Connectivity Foundation
- Open Mobile Alliance
- OpenAPI
- OpenFog Agility Pillar
- OpenFog Architecture Whitepaper
- OpenFog AutonomyPillar
- OpenFog Consortium
- OpenFog Data Analytics and Control Perspective
- OpenFog Deployment Viewpoint
- OpenFog Functional Viewpoint
- OpenFog Hierarchy Pillar
- OpenFog IT Business and Cross-fog Applications Perspective
- OpenFog Manageability Perspective
- OpenFog Node View
- OpenFog Opennes Pillar
- OpenFog Programmability Pillar
- OpenFog RAS Pillar
- OpenFog Reference Architecture
- OpenFog Reference Architecture for Fog Computing
- OpenFog Scalability Pillar
- OpenFog Security Perspective
- OpenFog Security Pillar
- OpenFog System Architecture View
- ORION Context Broker
- Performance
- Performance and Scale Perspective
- Periodic Communication
- Physical Connectivity
- Physical Web
- Platform Industry 4.0
- Privacy
- Product Liability
- Product Manager
- Programmability
- project manager
- Provenance Tracking
- Pseudonimity
- Quality of Service
- r a m i assetlayer anno
- r a m i body anno
- r a m i business layer anno
- r a m i communicationlayer anno
- r a m i connected world
- r a m i connected world anno
- r a m i control device anno
- r a m i enterprise anno
- r a m i field device
- r a m i field device anno
- r a m i functional layer anno
- r a m i header anno
- r a m i information layer anno
- r a m i integration layer anno
- r a m i product
- r a m i product anno
- r a m i station anno
- r d f
- Radio activity control
- RAMI Asset Layer
- RAMI Business Layer
- RAMI Communication Layer
- RAMI Functional Layer
- RAMI Information Layer
- RAMI Integration Layer
- RAML
- Reactive Streams
- Real Time Analytics
- Regulatory Compliance
- Reliability
- Resilience
- REST
- Return On Investment
- RFC 1122
- RFC 5246
- RFC 6750
- RFC 7252
- RFC 7642
- RFC 7643
- RFC 7644
- RFC 768
- RFC 793
- Risk Management
- Role Categorization
- ROLL
- RPMA
- Safety
- Scalability
- SCIM
- Secure Communication
- Security
- Security Configuration
- Selection of Service Provider
- Semantic Interoperability
- Sensing
- Service Access Control
- Service Choreography
- Service Composition
- Service Deployment
- Service Description
- Service Discovery
- Service Isolation
- Service level agreement
- Service life-cycle management
- Service Orchestration
- Service Recovery
- Service Selection
- Software Updates
- Spatial modeling
- Stream processing
- Syntactic Interoperability
- System Engineer
- System evolution
- system operator
- System Recovery
- The Industrial Internet of Things Volume G1: Reference Architecture IIC:PUB:G1:V1.80:20170131
- The Industrial Internet of Things Volume G5: Connectivity Framework
- Thing description
- Thing mobility
- Thing representation
- Time Synchronization
- Trusted Connector
- Trustworthiness
- Unicast
- Unreliable Network
- User Interaction
- User Preferences
- Vendor Lockin
- Virtual Entity
- x a c m l
- x road deployment view anno
- x road protocols interfaces anno
- x road system components anno
- x road technology matrix anno
- x-road
- X-Road Architecture Technical Specification Version: 1.0 18.09.2015 15 pages Doc. ID: ARC-G
- x-road Deplyoment View
- x-road Protocols and Interfaces
- x-road System Components
- x-road Technology Matrix
- x-Tee
6LoWPANni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#LoWPAN
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- maker op i e t f
- has Classification op IIRA Connectivity
- has Classification op RAMI Communication Layer
- has Developer op i e t f
- has Publisher op i e t f
- has d bpedia resource dp 6 lo w p a n
- has wikipedia article dp 6 lo w p a n
- has Target Concern op communication
Access Policyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AccessPolicy
- belongs to
- Concern c
- has facts
- supports op Data Access Control
Access Rights for IoT-Cloudni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Access_Rights_for_IoT-Cloud
- belongs to
- Concern c
- has facts
- supports op cloud connectivity
- has wikipedia article dp access rights
Accountabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Accountability
- belongs to
- Concern c
Actuationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Actuation
Adaptabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Adaptability
Administration Shellni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AdministrationShell
- belongs to
- Standard Classification c
- Standarization Framework c
- has facts
- associated with op Trusted Connector
- has Publisher op Platform Industry 4.0
- alignes With op Trusted Connector
- frames op lifecycle status
- frames op Availability
- frames op Business Context
- frames op communication
- frames op Data Access
- frames op Dynamic Adjustability
- frames op Endpoint Invocation
- frames op Identification
- frames op Identity Management
- frames op Integrity Protection and Verification
- frames op Interoperability
- frames op Secure Communication
- frames op Security
- frames op Semantic Interoperability
- frames op Service Choreography
- frames op Service Composition
- frames op Service Orchestration
- frames op Syntactic Interoperability
- frames op Thing description
- frames op Thing representation
- frames op Trustworthiness
Administration Shell Headerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIHeader
- belongs to
- Standard Classification c
- Standarization Framework c
- has facts
- has Publisher op Platform Industry 4.0
- frames op lifecycle status
- frames op Business Context
- frames op Data Access
- frames op Endpoint Invocation
- frames op Identification
- frames op Identity Management
- frames op Interoperability
- frames op Security
- frames op Semantic Interoperability
- frames op Syntactic Interoperability
- frames op Thing description
- frames op Thing representation
- frames op Trustworthiness
Aeronni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Aeron
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp aeron
agilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Agility
- belongs to
- Concern c
- has facts
- supports op Business Context
aii data annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AiiDataAnno
- belongs to
- oa annotation c
AII Data Classificationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AiiData
- belongs to
- Alliance of Industrial Internet Architecture Classification c
- has facts
- is Described in op AII Industrial Internet Architecture
- alignes With op IDS RAM Information Layer
- alignes With op information domain
- frames op Data Analytics
- frames op Data Processing
- frames op Data Collection
- frames op Edge computing
- frames op Semantic Interoperability
AII Industrial Internet Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IndustrialInternetArchitecture
- belongs to
- Architecture Description c
- has facts
- has Publisher op Alliance of Industrial Internet
- has official resource dp industrial.pdf
aii network annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AiiNetworkAnno
- belongs to
- oa annotation c
AII Network Classificationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AiiNetwork
- belongs to
- Alliance of Industrial Internet Architecture Classification c
- has facts
- is Described in op AII Industrial Internet Architecture
- alignes With op IDS RAM System Layer
- alignes With op IIRA Connectivity
- alignes With op RAMI Communication Layer
- alignes With op RAMI Integration Layer
- frames op communication
- frames op Connectivity
- frames op Identification
- frames op Syntactic Interoperability
aii security annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AiiSecurityAnno
- belongs to
- oa annotation c
AII Security Classificationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AiiSecurity
Alliance Industrie du Futurni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AllianceIndustrieDuFutur
- belongs to
- i io t consortium c
- has facts
- has Headquater In op france
- has official resource dp http://www.industrie-dufutur.org/
Alliance of Industrial Internetni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AllianceOfIndustrialInternet
- belongs to
- i io t consortium c
- has facts
- has Headquater In op china
Alljoynni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Alljoyn
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp framework
AllSeen Allianceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AllSeenAlliance
- belongs to
- organization c
- i io t consortium c
- has facts
- has official resource dp allseenalliance-org:
AMQPni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AMQP
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp http://www.amqp.org/
anno actuationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AnnoActuation
- belongs to
- oa annotation c
anno aii classificationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AnnoAiiClassification
- belongs to
- oa annotation c
Anonymityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Anonymity
Arrowhead Frameworkni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ArrowheadFramework
- belongs to
- i io t consortium c
- Standarization Framework c
- has facts
- has Publisher op Arrowhead Project
Arrowhead Projectni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ArrowheadProject
- belongs to
- organization c
Artificial Intelligenceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AI
- belongs to
- Concern c
- has facts
- supports op Data Analytics
- has d bpedia resource dp ""@en
- has d bpedia resource dp artificial intelligence
Asset Managementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AssetManagement
Authenticationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Authentication
- belongs to
- Concern c
- has facts
- supports op Identity Management
authorizationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Authorization
Auto Scalingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Auto_Scaling
- belongs to
- Concern c
- has facts
- supports op Scalability
- has wikipedia article dp autoscaling
Autonomous Communicationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AutonomousCommunication
- belongs to
- Concern c
- has facts
- supports op communication
- supports op Service Choreography
Autonomous Configurationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#AutonomousConfiguration
- belongs to
- Concern c
- has facts
- supports op Service Choreography
Availabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Availability
- belongs to
- Concern c
- has facts
- supports op Reliability
- has d bpedia resource dp availability
Awarenessni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Awareness
- belongs to
- Concern c
- has facts
- supports op Edge computing
- has wikipedia article dp awareness
Bandwidthni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Bandwidth
- belongs to
- Concern c
- has facts
- supports op communication
- has wikipedia article dp bandwidth (computing)
BDV SRIA European Big Data Value Strategic Research and Innovation Agenda version 4.0 October 2017ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#European_BDV_SRIA_version_4_0
- belongs to
- oa specific resource c
BDVA Cloud and High Performance Computingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaCloudAndHighPerformanceComputing
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- associated with op IIRA Application Domain
- is Described in op BDVA SIRA
- alignes With op IIRA Application Domain
- frames op Artificial Intelligence
- frames op Big Data Applications
- frames op Cloud Computing Capability
- frames op Data Analytics
- frames op Data Processing
- frames op Data Publishing
- frames op Machine Learning
bdva cloud and high performance computing annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaCloudAndHighPerformanceComputingAnno
- belongs to
- oa annotation c
BDVA Communication and Connectivityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaCommunicationConnectivity
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- is Described in op BDVA SIRA
- frames op communication
- frames op Data Access
- frames op Data Analytics
- frames op Interoperability
- frames op Quality of Service
- frames op Semantic Interoperability
- frames op Service Description
bdva communication connectivity annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaCommunicationConnectivityAnno
- belongs to
- oa annotation c
BDVA Concernni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaConcern
- belongs to
- class
- is also defined as
- class
bdva concern annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaConcernAnno
- belongs to
- oa annotation c
bdva cyber security trust annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaCyberSecurityTrustAnno
- belongs to
- oa annotation c
BDVA Cybersecurity and Trustni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaCyberSecurityTrust
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- associated with op security
- associated with op IDS RAM Security Perspective
- associated with op IIC Security Framework
- is Described in op BDVA SIRA
- alignes With op security
- alignes With op IDS RAM Security Perspective
- alignes With op IIC Security Framework
- frames op communication
- frames op Data Sovereignty
- frames op Integrity Protection and Verification
- frames op Privacy
- frames op Secure Communication
- frames op Security
- frames op Trustworthiness
BDVA Data Analyticsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataAnalytics
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- associated with op IDS RAM Process Layer
- associated with op information domain
- associated with op RAMI Functional Layer
- associated with op RAMI Information Layer
- is Described in op BDVA SIRA
- alignes With op IDS RAM Process Layer
- alignes With op information domain
- alignes With op RAMI Functional Layer
- alignes With op RAMI Information Layer
- frames op Artificial Intelligence
- frames op Data Analytics
- frames op Data Processing
- frames op Machine Learning
- frames op Stream processing
- frames op Trustworthiness
bdva data analytics annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataAnalyticsAnno
- belongs to
- oa annotation c
BDVA Data Managementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataManagement
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- associated with op IDS RAM Information Layer
- associated with op IDS RAM Process Layer
- associated with op RAMI Information Layer
- is Described in op BDVA SIRA
- alignes With op IDS RAM Information Layer
- alignes With op IDS RAM Process Layer
- alignes With op RAMI Information Layer
- frames op Big Data Applications
- frames op Data Quality
- frames op Interoperability
- frames op Provenance Tracking
- frames op Security
- frames op Semantic Interoperability
- frames op Syntactic Interoperability
- frames op Trustworthiness
bdva data management annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataManagementAnno
- belongs to
- oa annotation c
BDVA Data Processing Architecturesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataProcessingArchitectures
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- associated with op IDS RAM Process Layer
- associated with op IIRA Connectivity
- associated with op information domain
- is Described in op BDVA SIRA
- alignes With op IDS RAM Process Layer
- alignes With op IIRA Connectivity
- alignes With op information domain
- frames op Big Data Applications
- frames op communication
- frames op Data at rest
- frames op data in motion
- frames op Data Processing
- frames op Scalability
- frames op Stream processing
bdva data processing architectures annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataProcessingArchitecturesAnno
- belongs to
- oa annotation c
BDVA Data Protectionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataProtection
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- associated with op IDS RAM Security Perspective
- associated with op IIC Security Framework
- is Described in op BDVA SIRA
- alignes With op IDS RAM Security Perspective
- alignes With op IIC Security Framework
- frames op Data Protection
- frames op Data Sovereignty
- frames op Privacy
- frames op Trustworthiness
bdva data protection annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataProtectionAnno
- belongs to
- oa annotation c
BDVA Data Sharing Platformsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataSharingPlatforms
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- associated with op IDS RAM
- associated with op Industrial Internet Reference Architecture
- is Described in op BDVA SIRA
- frames op Business Context
- frames op Data Economy
- frames op Data Publishing
bdva data sharing platforms annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataSharingPlatformsAnno
- belongs to
- oa annotation c
bdva data visualization and user interaction annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataVisualizationAndUserInteractionAnno
- belongs to
- oa annotation c
bdva development engineering annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDevelopmentEngineeringAnno
- belongs to
- oa annotation c
BDVA Engineering and DevOpsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDevelopmentEngineering
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- is Described in op BDVA SIRA
BDVA IoT CPS and Edge Computingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaThingsAssetsSensorsActuators
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- is Described in op BDVA SIRA
- frames op IoT
BDVA SIRAni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaSira
- belongs to
- Standarization Framework c
- has facts
- has Publisher op Big Data Value Association
bdva sira annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaSiraAnno
- belongs to
- oa annotation c
BDVA Standardsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaStandards
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- is Described in op BDVA SIRA
- frames op Business Context
- frames op communication
- frames op Data Economy
- frames op Interoperability
bdva standards annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaStandardsAnno
- belongs to
- oa annotation c
bdva things assets sensors actuators annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaThingsAssetsSensorsActuatorsAnno
- belongs to
- oa annotation c
Big Data Applicationsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BigDataApplications
- belongs to
- Concern c
- has facts
- supports op Data Analytics
- has d bpedia resource dp big data
Big Data Value Associationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BDVA
- belongs to
- organization c
Blockchainni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Blockchain
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has d bpedia resource dp blockchain.info
Bluetoothni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Bluetooth
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has Classification op r a m i communication layer
- has official resource dp bluetooth home.aspx
BPMni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BusinessProcessManagement
- belongs to
- Concern c
- has facts
- supports op Business Context
- has d bpedia resource dp business process management
Business Contextni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BusinessContext
- belongs to
- Concern c
- has facts
- has d bpedia resource dp electronic business
Business Transactionsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BusinessTransactions
- belongs to
- Concern c
- has facts
- supports op Business Context
- has d bpedia resource dp financial transaction
Business Valueni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BusinessValue
- belongs to
- Concern c
- has facts
- supports op Business Context
cardinality of data sourcesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#CardinalityOfDataSources
- belongs to
- Concern c
- has facts
- supports op Interoperability
Cardinality of Participantsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#CardinalityOfParticipants
- belongs to
- Concern c
- has facts
- supports op interoperability
- has d bpedia resource dp cardinality (computer engineering)
CEPni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ComplexEventProcessing
- belongs to
- Concern c
- has facts
- supports op Data Analytics
- has d bpedia resource dp complex event processing
Certificationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Certification
- belongs to
- Concern c
- has facts
- supports op Security
- supports op Trustworthiness
- has d bpedia resource dp certification
Cloud Computing Capabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#CloudComputing
- belongs to
- Concern c
- has facts
- has d bpedia resource dp cloud computing
cloud connectivityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Cloud_Connectivity
- has facts
- supports op Cloud Computing Capability
CoAPni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_8323
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- maker op i e t f
- has Classification op IIRA Connectivity
- has Classification op RAMI Communication Layer
- has Developer op i e t f
- has Publisher op i e t f
- has d bpedia resource dp constrained application protocol
- has official resource dp rfc8323
- has wikipedia article dp constrained application protocol
communicationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Communication
- belongs to
- Admin Shell Sub Model c
- Concern c
- Standard Classification c
- has facts
- is Described in op Administration Shell
- supports op Interoperability
Complianceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Compliance
- belongs to
- Concern c
- has facts
- supports op Reliability
- has d bpedia resource dp regulatory compliance
Confidentialityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Confidentiality
Connectivityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Connectivity
- belongs to
- Concern c
- has facts
- supports op Syntactic Interoperability
- has d bpedia resource dp connectivity
- has wikipedia article dp connectivity
Constrained Devicesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ConstrainedDevices
Context Awarenessni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ContextAwareness
- belongs to
- Concern c
- has facts
- supports op Autonomous Communication
- has d bpedia resource dp context awareness
Cost Efficiencyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#CostEfficiency
- belongs to
- Concern c
- has facts
- supports op Business Context
Cross-domain Identity Managementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#CrossDomainIdentityManagement
- belongs to
- Concern c
- has facts
- supports op Identity Management
- has d bpedia resource dp system for cross domain identity management
customerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Customer
- belongs to
- Stakeholder Group c
Customizationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Customization
- belongs to
- Concern c
- has facts
- supports op Business Context
- supports op Scalability
- has wikipedia article dp customization
Customizationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataEncryption
- belongs to
- Concern c
- has facts
- supports op Business Context
- supports op Secure Communication
- has wikipedia article dp customization
- has wikipedia article dp encryption
d i n e n 50128ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_EN_50128
d i n e n 50159ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_EN_50159
- belongs to
- Standard c
- has facts
- has Classification op IDS RAM Certification Perspective
- has Target Concern op Safety
d i n e n i s o 13849ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_EN_ISO_13849
- belongs to
- Standard c
- has facts
- has Classification op IDS RAM Certification Perspective
- has Target Concern op Safety
d i n e n i s o i e c 17025ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_EN_ISO_IEC_17025
- belongs to
- Standard c
- has facts
- has Classification op IDS RAM Certification Perspective
d i n i s o 14638ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_ISO_14638
- belongs to
- Standard c
- has facts
- frames op Thing description
d i n s p e c 16593 p1ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_SPEC_16593_P1
- belongs to
- Standard c
- has facts
- frames op Service Description
d i n s p e c 92222ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_SPEC_92222
- belongs to
- Standard c
- has facts
- frames op Cloud Computing Capability
- frames op communication
- frames op interoperability
Data Accessni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataAccess
- belongs to
- Concern c
- has facts
- has d bpedia resource dp data access
Data Access Controlni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataAccessControl
- belongs to
- Concern c
- has facts
- supports op authorization
- has d bpedia resource dp access control
Data Aggregationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataAggregation
- belongs to
- Concern c
- has facts
- has wikipedia article dp data aggregation
Data Analyticsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataAnalytics
- belongs to
- Concern c
- has facts
- has d bpedia resource dp data analysis
Data at restni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataAtRest
- belongs to
- Concern c
- has facts
- supports op communication
- has d bpedia resource dp data at rest
Data Collectionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Data_Collection
- belongs to
- Concern c
- has facts
- supports op Data Analytics
- has d bpedia resource dp data collection
- has wikipedia article dp data collection
Data Confidentialityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Data_Confidentiality
data consumerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataConsumer
- belongs to
- Stakeholder Group c
Data Descriptionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataDescription
- belongs to
- Concern c
- has facts
- supports op Semantic Interoperability
Data Discoveryni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataDiscovery
- belongs to
- Concern c
- has facts
- supports op Interoperability
Data Economyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataEconomy
- belongs to
- Concern c
- has facts
- supports op Business Context
- has d bpedia resource dp digital economy
Data Integrityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataIntegrity
Data Isolationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataIsolation
- belongs to
- Concern c
- has facts
- supports op Data Integrity
- has wikipedia article dp isolation (database systems)
Data lifecycle managementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataLifecycleManagment
- belongs to
- Concern c
- has facts
- supports op Data Analytics
- has d bpedia resource dp information lifecycle management
Data Locationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataLocation
- belongs to
- Concern c
- has facts
- supports op Data Usage Control
Data Marketsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataMarkets
- belongs to
- Concern c
- has facts
- supports op Data Economy
data ownerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataOwner
- belongs to
- Stakeholder Group c
Data Ownershipni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataOwnership
Data Processingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataProcessing
- belongs to
- Concern c
- has facts
- has d bpedia resource dp data processing
Data Protectionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataProtection
- belongs to
- Concern c
- is same as
- data security
- has facts
- supports op Privacy
- has d bpedia resource dp information privacy
data providerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataProvider
- belongs to
- Stakeholder Group c
Data Publishingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataPublishing
- belongs to
- Concern c
- has facts
- supports op Data Access Control
Data Qualityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataQuality
- belongs to
- Concern c
- has facts
- supports op Quality of Service
- has d bpedia resource dp data quality
data securityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataSecurity
- belongs to
- Concern c
- is same as
- Data Protection
- has facts
- has wikipedia article dp data security
Data Sovereigntyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataSovereignty
- belongs to
- Concern c
- Standard Classification c
- has facts
- has d bpedia resource dp cyber sovereignty
- has wikipedia article dp data sovereignty
Data Storageni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataStorage
- belongs to
- Concern c
- has facts
- supports op Data Processing
- has wikipedia article dp data storage
Data Transfer Projectni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataTransferProject
- belongs to
- organization c
- Data Sharing Initiative c
- has facts
- associated with op Data Transfer Project Architecture
- has official resource dp data transfer project
data transfer project annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataTransferProjectAnno
- belongs to
- oa annotation c
Data Transfer Project Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DtpArchitecture
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- has Publisher op Data Transfer Project
Data Transfer Project Overview and Fundamentalsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Data_Transfer_Project_Overview_and_Fundamentals
- belongs to
- oa specific resource c
Data Transfer Project Whitepaperni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataTransferProjectWhitepaper
- belongs to
- document c
- Publication
- has facts
- maker op Data Transfer Project
- has Classification op DTP Deployment
- has Classification op DTP Ecosystem
- has Classification op DTP Security & Privacy
- has Classification op DTP System
- has Developer op Data Transfer Project
- has Publisher op Data Transfer Project
- has d bpedia resource dp data transfer project
- has wikipedia article dp data transfer project
- has Target Concern op Data Sovereignty
- has Target Concern op Identity Management
- has Target Concern op Privacy
- has Target Concern op Secure Communication
- has Target Concern op User Preferences
Data Usage Controlni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataUsageControl
- belongs to
- Concern c
- has facts
- supports op authorization
Data Visualisation and User Interactionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#BdvaDataVisualizationAndUserInteraction
- belongs to
- BDVA Concern c
- Standard Classification c
- has facts
- associated with op IIRA Usage Viewpoint
- associated with op RAMI Functional Layer
- is Described in op BDVA SIRA
- alignes With op IIRA Usage Viewpoint
- alignes With op RAMI Functional Layer
- frames op Big Data Applications
Decision makerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DecisionMaker
- belongs to
- Layer c
developerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Developer
- belongs to
- Stakeholder Group c
Device Authenticationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Device_Authentication
- belongs to
- Concern c
- has facts
- supports op Authentication
- has wikipedia article dp authentication
Device Securityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DeviceSecurity
- belongs to
- Concern c
- has facts
- supports op Objects Safety and Security
DIN 77005-1:2018-09ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_77005_P1
- belongs to
- Standard c
- has facts
- frames op Data lifecycle management
DIN EN 50129ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_EN_50129
- belongs to
- Standard c
- has facts
- has Classification op IDS RAM Certification Perspective
- has Target Concern op Safety
DIN EN 50155ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_EN_50155
- belongs to
- Standard c
- has facts
- has Classification op IDS RAM Certification Perspective
- has Target Concern op Safety
DIN EN 61511ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DIN_EN_61511
- belongs to
- Standard c
- has facts
- has Classification op IDS RAM Certification Perspective
- has Target Concern op Safety
DMAni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DataMarketAustria
- belongs to
- organization c
- Data Sharing Initiative c
- StandardOrganization c
- has facts
- has official resource dp http://www.datamarket.at/
DMA Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DmaArchitecture
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- has Publisher op DMA
DMA Service Technology Specification and Development Roadmapni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DmaServiceTechnologySpecificationAndDevelopmentRoadmap
- belongs to
- document c
- Publication
- Standarization Framework c
- has facts
- associated with op Blockchain
- associated with op REST
- associated with op RFC 6750
- maker op DMA
- has Publisher op DMA
- has official resource dp d m a deliverable d6.1 f i n a l v01.pdf
- has Target Concern op Authentication
- has Target Concern op authorization
- has Target Concern op Big Data Applications
- has Target Concern op billing
- has Target Concern op Cloud Computing Capability
- has Target Concern op Data Access
- has Target Concern op Data Quality
- has Target Concern op Privacy
- has Target Concern op Secure Communication
- has Target Concern op Security
- has Target Concern op Semantic Interoperability
- has Target Concern op Stream processing
- has Target Concern op Syntactic Interoperability
- has Target Concern op Trustworthiness
DTP Deploymentni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DtpDeploymentView
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IDS RAM Process Layer
- associated with op IIRA Implementation Viewpoint
- is Described in op Data Transfer Project Architecture
- alignes With op IDS RAM Process Layer
- alignes With op IIRA Implementation Viewpoint
- frames op Identification
- frames op Identity Management
- frames op Security
- frames op Service Deployment
- frames op Service life-cycle management
- frames op Trustworthiness
- frames op User Interaction
DTP Ecosystemni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DtpEcosystemView
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IDS RAM Governance Perspective
- associated with op IIRA Usage Viewpoint
- is Described in op Data Transfer Project Architecture
- alignes With op IDS RAM Governance Perspective
- alignes With op IIRA Usage Viewpoint
DTP Security & Privacyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DtpSecurityPrivacy
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op security
- associated with op IDS RAM Governance Perspective
- associated with op IIRA Privacy
- associated with op IIRA Security
- is Described in op Data Transfer Project Architecture
- alignes With op security
- alignes With op IDS RAM Governance Perspective
- alignes With op IIRA Privacy
- alignes With op Security
DTP Systemni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DtpSystemView
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IDS RAM System Layer
- associated with op IIRA Connectivity
- associated with op IIRA Operation Domain
- associated with op information domain
- associated with op RAMI Functional Layer
- associated with op RAMI Integration Layer
- associated with op RFC 6750
- is Described in op Data Transfer Project Architecture
- alignes With op IDS RAM System Layer
- alignes With op IIRA Connectivity
- alignes With op IIRA Operation Domain
- alignes With op information domain
- alignes With op RAMI Functional Layer
- alignes With op RAMI Integration Layer
- frames op Authentication
- frames op communication
- frames op Data Access
- frames op Interoperability
- frames op Secure Communication
- frames op Security
- frames op Semantic Interoperability
- frames op Syntactic Interoperability
- frames op Trustworthiness
Dynamic Adjustabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DynamicAdjustability
- belongs to
- Concern c
- has facts
- supports op Service Choreography
- supports op Service Composition
- supports op Service Orchestration
Dynamic Discoveryni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#DynamicDiscovery
- belongs to
- Concern c
- has facts
- supports op Data Discovery
- supports op Service Discovery
Edge Analyticsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgeAnalytics
- belongs to
- Concern c
- has facts
- has wikipedia article dp edge computing
Edge computingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgeComputing
- belongs to
- Concern c
- has facts
- supports op Cloud Computing Capability
- supports op Data Processing
- has d bpedia resource dp edge computing
Edgecross Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossArchitecture
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- has Publisher op Edgecross Consortium
Edgecross Consortiumni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossConsortium
- belongs to
- organization c
- i io t consortium c
- StandardOrganization c
- has facts
- has official resource dp https://www.edgecross.org/en/
Edgecross Consortium to Address Edge Integration in IIoT-enabled Architecturesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Edgecross_Consortium_to_Address_Edge_Integration_in_IIoT_enabled_Architectures
- belongs to
- oa specific resource c
edgecross edge computing layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossEdgeComputingLayerAnno
- belongs to
- oa annotation c
Edgecross Edgecomputing Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossEdgeComputingLayer
- belongs to
- Edgecross Layer c
- Standard Classification c
- has facts
- associated with op IDS RAM System Layer
- associated with op IIRA Control Domain
- associated with op IIRA Operation Domain
- associated with op information domain
- associated with op RAMI Information Layer
- associated with op RAMI Integration Layer
- is Described in op Edgecross Architecture
- alignes With op IDS RAM System Layer
- alignes With op IIRA Control Domain
- alignes With op IIRA Operation Domain
- alignes With op information domain
- alignes With op RAMI Information Layer
- alignes With op RAMI Integration Layer
- frames op Cloud Computing Capability
- frames op Data Processing
- frames op Edge computing
- frames op Interoperability
- frames op Semantic Interoperability
Edgecross FAni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossFacilityLayer
- belongs to
- Edgecross Layer c
- Standard Classification c
- has facts
- associated with op IIRA Physical Systems
- associated with op RAMI Asset Layer
- is Described in op Edgecross Architecture
- alignes With op IIRA Physical Systems
- alignes With op RAMI Asset Layer
edgecross facility layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossFacilityLayerAnno
- belongs to
- oa annotation c
Edgecross IT Systems Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossItSystemsLayer
- belongs to
- Edgecross Layer c
- Standard Classification c
- has facts
- associated with op IDS RAM System Layer
- associated with op IIRA Application Domain
- associated with op RAMI Integration Layer
- is Described in op Edgecross Architecture
- alignes With op IDS RAM System Layer
- alignes With op IIRA Application Domain
- alignes With op RAMI Integration Layer
- frames op communication
- frames op Data Analytics
- frames op data in motion
edgecross it systems layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossItSystemsLayerAnno
- belongs to
- oa annotation c
edgecross layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossLayerAnno
- belongs to
- oa annotation c
Edgecross Whitepaperni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EdgecrossWhitepaper
- belongs to
- document c
- Publication
- has facts
- maker op Edgecross Consortium
- has Classification op Edgecross Edgecomputing Layer
- has Classification op Edgecross FA
- has Classification op Edgecross IT Systems Layer
- has Publisher op Edgecross Consortium
- has official resource dp edgecross consortium w p( e).pdf
- has Target Concern op Edge computing
- has Target Concern op Interoperability
end userni back to ToC or Named Individual ToC
IRI: http://purl.oclc.org/NET/mvco.owl#EndUser
- belongs to
- Stakeholder Group c
Endpoint Descriptionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EndpointDescription
- belongs to
- Concern c
- has facts
- supports op Semantic Interoperability
Endpoint Invocationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EndpointInvocation
- belongs to
- Concern c
- has facts
- supports op Syntactic Interoperability
Energy Controlni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EnergyControl
- belongs to
- Concern c
- has facts
- supports op Energy Efficiency
- has wikipedia article dp energy management
Energy Efficiencyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EnergyEfficiency
- belongs to
- Admin Shell Sub Model c
- Concern c
- Standard Classification c
- has facts
- is Described in op Administration Shell
- supports op IoT
- has wikipedia article dp efficient energy use
Event-Driven Messagingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#EventDrivenMessaging
- belongs to
- Concern c
- has facts
- supports op data in motion
- has d bpedia resource dp event driven messaging
Evolvabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Evolvability
- belongs to
- Concern c
- has facts
- supports op Dynamic Adjustability
- has d bpedia resource dp evolving intelligent system
- has d bpedia resource dp software evolution
Execution Variabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ExecutionVariability
- belongs to
- Concern c
Extensibilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Extensibility
- belongs to
- Concern c
- has facts
- supports op Evolvability
- has wikipedia article dp extensibility
f i w a r e annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FIWAREAnno
- belongs to
- oa annotation c
Fairnessni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Fairness
- belongs to
- Concern c
- has facts
- supports op Business Context
- has wikipedia article dp fairness
Fault Toleranceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FaultTolerance
- belongs to
- Concern c
- has facts
- supports op Availability
- has d bpedia resource dp category: fault tolerant computer systems
- has wikipedia article dp fault tolerance
FIWAREni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Fiware
- belongs to
- organization c
fiware advanced ui annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareAdvancedUiAnno
- belongs to
- oa annotation c
FIWARE Advanced Web-based User Interfaceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareAdvancedUi
- belongs to
- Fiware Chapter c
- Standard Classification c
- has facts
- associated with op end user
- associated with op IIRA Application Domain
- associated with op IIRA Usage Viewpoint
- is Described in op FIWARE Architecture
- alignes With op IIRA Application Domain
- alignes With op IIRA Usage Viewpoint
- frames op User Interaction
FIWARE Applications Services and Data Deliveryni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareApplicationsServicesAndDataDelivery
- belongs to
- Fiware Chapter c
- Standard Classification c
- has facts
- associated with op IDS RAM Process Layer
- associated with op IIRA Connectivity
- associated with op NGSI-LD Architecture
- is Described in op FIWARE Architecture
- alignes With op IDS RAM Process Layer
- alignes With op IIRA Connectivity
- alignes With op NGSI-LD Architecture
- frames op Data Analytics
- frames op data selection
- frames op Service Composition
- frames op Service Selection
fiware applications services and data delivery annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareApplicationsServicesAndDataDeliveryAnno
- belongs to
- oa annotation c
FIWARE Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FIWARE
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- associated with op IDS RAM System Layer
- associated with op IIRA Implementation Viewpoint
- has Publisher op FIWARE
- alignes With op IDS RAM System Layer
- alignes With op IIRA Implementation Viewpoint
- has official resource dp https://www.fiware.org/
fiware chapter annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareChapterAnno
- belongs to
- oa annotation c
FIWARE Cloud Hostingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareCloudHosting
- belongs to
- Fiware Chapter c
- Standard Classification c
- has facts
- associated with op IDS RAM System Layer
- associated with op IIRA Application Domain
- associated with op IIRA Distributed Data Management
- associated with op IIRA Scalability
- associated with op NGSI-LD Architecture
- is Described in op FIWARE Architecture
- alignes With op IDS RAM System Layer
- alignes With op IIRA Application Domain
- alignes With op IIRA Distributed Data Management
- alignes With op IIRA Scalability
- alignes With op NGSI-LD Architecture
- frames op Availability
- frames op Cloud Computing Capability
- frames op Data Processing
- frames op Data Sovereignty
- frames op Integrity Protection and Verification
- frames op Privacy
- frames op Reliability
- frames op Safety
- frames op Security
- frames op Service Composition
- frames op Service Deployment
- frames op Service life-cycle management
- frames op Service Orchestration
- frames op Trustworthiness
fiware cloud hosting annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareCloudHostingAnno
- belongs to
- oa annotation c
fiware data context management annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareDataContextManagementAnno
- belongs to
- oa annotation c
FIWARE Data/Context Managementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareDataContextManagement
- belongs to
- Fiware Chapter c
- Standard Classification c
- has facts
- associated with op NGSI-LD API Operation
- associated with op NGSI-LD Data Representation
- associated with op NGSI-LD Information Model
- is Described in op FIWARE Architecture
- alignes With op NGSI-LD API Operation
- alignes With op NGSI-LD Data Representation
- alignes With op NGSI-LD Information Model
- frames op Big Data Applications
- frames op Data Discovery
- frames op Data Processing
- frames op Interoperability
- frames op Stream processing
FIWARE Interface to Networks and Devicesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#InterfaceNetworksDevices
- belongs to
- Fiware Chapter c
- Standard Classification c
- has facts
- associated with op IDS RAM Process Layer
- associated with op IDS RAM System Layer
- associated with op NGSI-LD Architecture
- associated with op open daylight
- is Described in op FIWARE Architecture
- alignes With op IDS RAM Process Layer
- alignes With op IDS RAM System Layer
- alignes With op NGSI-LD Architecture
- frames op Cloud Computing Capability
- frames op Data Description
- frames op Data Processing
- frames op Data Sovereignty
- frames op Endpoint Description
- frames op Endpoint Invocation
- frames op Interoperability
- frames op IoT
- frames op Privacy
- frames op Quality of Service
- frames op Scalability
- frames op Security
- frames op Semantic Interoperability
- frames op Service Composition
- frames op Service Description
- frames op Service Orchestration
- frames op Syntactic Interoperability
- frames op Trustworthiness
FIWARE IoT Services Enablementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareIotServicesEnablement
- belongs to
- Fiware Chapter c
- Standard Classification c
- has facts
- associated with op IDS RAM System Layer
- associated with op IIRA Control Domain
- associated with op RAMI Communication Layer
- associated with op RAMI Integration Layer
- is Described in op FIWARE Architecture
- alignes With op IDS RAM System Layer
- alignes With op IIRA Control Domain
- alignes With op RAMI Communication Layer
- alignes With op RAMI Integration Layer
- frames op Cloud Computing Capability
- frames op Data Discovery
- frames op Data Processing
- frames op Edge computing
- frames op Endpoint Invocation
- frames op Interoperability
- frames op IoT
- frames op Syntactic Interoperability
fiware iot services enablement annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareIotServicesEnablementAnno
- belongs to
- oa annotation c
FIWARE Securityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareSecurity
- belongs to
- Fiware Chapter c
- Standard Classification c
- has facts
- associated with op security
- associated with op IDS RAM Security Perspective
- associated with op IIRA Security
- associated with op x a c m l
- is Described in op FIWARE Architecture
- alignes With op security
- alignes With op IDS RAM Security Perspective
- alignes With op IIRA Security
- frames op Authentication
- frames op authorization
- frames op Data Access Control
- frames op Data Sovereignty
- frames op Identity Management
- frames op Privacy
- frames op Security
- frames op Trustworthiness
fiware security annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#FiwareSecurityAnno
- belongs to
- oa annotation c
Geo trackingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#GeoTracking
- belongs to
- Concern c
- has facts
- supports op Context Awareness
- has d bpedia resource dp track and trace
Geospatial data and informationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#GeospatialData
- belongs to
- Concern c
- has facts
- supports op Data Analytics
- has d bpedia resource dp geographic data and information
governanceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Governance
- belongs to
- Concern c
- has facts
- supports op Business Context
Greening of IoTni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Greening_of_IoT
- belongs to
- Concern c
- has facts
- supports op Energy Control
- has wikipedia article dp green computing
HTTP/1.1ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_2616
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op i e t f
- has Classification op IDS RAM System Layer
- has Classification op IIRA Functional Viewpoint
- has Classification op RAMI Communication Layer
- has Classification op tansport layer
- has Publisher op i e t f
- has official resource dp rfc2817
- has official resource dp rfc2616
HTTP/2ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_7540
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op i e t f
- has Classification op IDS Interoperability
- has Classification op IDS RAM System Layer
- has Classification op IIRA Functional Viewpoint
- has Classification op RAMI Communication Layer
- has Classification op tansport layer
- has Publisher op i e t f
HTTPSni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_2818
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op i e t f
- has Classification op IDS RAM Security Perspective
- has Classification op IDS RAM System Layer
- has Publisher op i e t f
i d s r a m business layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMBusinessLayerAnno
- belongs to
- oa annotation c
i d s r a m certification annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMCertificationAnno
- belongs to
- oa annotation c
i d s r a m functional layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMFunctionalLayerAnno
- belongs to
- oa annotation c
i d s r a m governance annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMGovernanceAnno
- belongs to
- oa annotation c
i d s r a m information layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMInformationLayerAnno
- belongs to
- oa annotation c
i d s r a m layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMLayerAnno
- belongs to
- oa annotation c
i d s r a m process layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMProcessLayerAnno
- belongs to
- oa annotation c
i d s r a m security annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMSecurityAnno
- belongs to
- oa annotation c
i d s r a m system layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMSystemLayerAnno
- belongs to
- oa annotation c
i d4meni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ID4me
- belongs to
- Technical Specification c
- has facts
- has Target Concern op Identification
- has Target Concern op Identity Management
i e c 29115ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IEC_29115
- belongs to
- Standard c
- has facts
- has Classification op IIRA Security
- has Target Concern op Authentication
- has Target Concern op Identification
i e c 61508ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IEC_61508
- belongs to
- Standard c
- has facts
- has Classification op IDS RAM Certification Perspective
- has Classification op Safety
- has Target Concern op Safety
i e c 61511ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IEC_61511
- belongs to
- Standard c
- has facts
- has Classification op IDS RAM Certification Perspective
- has Target Concern op Safety
i e c 61804 p3ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IEC_61804_P3
- belongs to
- Standard c
- has facts
- frames op Thing description
i e c 61804 p4ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IEC_61804_P4
- belongs to
- Standard c
- has facts
- frames op Thing description
i e c 61804 p5ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IEC_61804_P5
- belongs to
- Standard c
- has facts
- frames op Thing description
i e c 61804 p6ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IEC_61804_P6
- belongs to
- Technical Report c
- has facts
- frames op Thing description
i e c 62264 p6ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IEC_62264_P6
- belongs to
- Standard c
- has facts
- frames op communication
i e c 62541ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IEC_62541
- belongs to
- Standard c
- has facts
- has Classification op communication
- has Classification op Data Sovereignty
- has Classification op IDS RAM System Layer
- has Classification op IICF Framework Layer
- has Classification op IIRA Application Domain
- has Classification op IIRA Operation Domain
- has Classification op information domain
- has Classification op RAMI Communication Layer
- has Classification op r a m i connected world
- has Classification op r a m i control device
- has Classification op r a m i enterprise
- has Classification op r a m i field device
- has Classification op r a m i station
- has Classification op r a m i work center
- has Classification op s c a d a level
- has Target Concern op Autonomous Communication
i i c f framework layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFFrameworkLayerAnno
- belongs to
- oa annotation c
i i c f link layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFLinkLayerAnno
- belongs to
- oa annotation c
i i c f network layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFNetworkLayerAnno
- belongs to
- oa annotation c
i i c f physical layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFPhysicalLayerAnno
- belongs to
- oa annotation c
i i c f tansport layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFTansportLayerAnno
- belongs to
- oa annotation c
i i r a application domain annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAApplicationDomainAnno
- belongs to
- oa annotation c
i i r a business domain annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRABusinessDomainAnno
- belongs to
- oa annotation c
i i r a business viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRABusinessViewpointAnno
- belongs to
- oa annotation c
i i r a connectivity annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAConnectivityAnno
- belongs to
- oa annotation c
i i r a control domain annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAControlDomainAnno
- belongs to
- oa annotation c
i i r a crosscutting function annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRACrosscuttingFunctionAnno
- belongs to
- oa annotation c
i i r a functional viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAFunctionalViewpointAnno
- belongs to
- oa annotation c
i i r a implementation viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAImplementationViewpointAnno
- belongs to
- oa annotation c
i i r a industrial analyticsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAIndustrialAnalytics
- belongs to
- IIRA Crosscutting Function c
- Standard Classification c
- has facts
- is Described in op Industrial Internet Reference Architecture
i i r a information domain annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAInformationDomainAnno
- belongs to
- oa annotation c
i i r a operations domain annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAOperationsDomainAnno
- belongs to
- oa annotation c
i i r a reliability annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAReliabilityAnno
- belongs to
- oa annotation c
i i r a resilience annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAResilienceAnno
- belongs to
- oa annotation c
i i r a safety annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRASafetyAnno
- belongs to
- oa annotation c
i i r a security annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRASecurityAnno
- belongs to
- oa annotation c
i i r a security framework annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRASecurityFrameworkAnno
- belongs to
- oa annotation c
i i r a usage viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAUsageViewpointAnno
- belongs to
- oa annotation c
i s o 13485ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ISO_13485
- belongs to
- Standard c
- has facts
- has Target Concern op Quality of Service
i s o 13849ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ISO_13849
- belongs to
- Standard c
- has facts
- has Classification op IDS RAM Certification Perspective
- has Classification op IIRA Security
- has Target Concern op Safety
i s o 19941ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ISO_19941
- belongs to
- Standard c
- has facts
- has Target Concern op Cloud Computing Capability
i s o 20140 p1ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ISO_20140_P1
- belongs to
- Standard c
- has facts
- frames op Energy Efficiency
Identificationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Identification
- belongs to
- Concern c
- Standard Classification c
- has facts
- associated with op identification
- associated with op i e c 24760
- associated with op i e c 62443
- associated with op i s o 24760
- alignes With op identification
- alignes With op i e c 24760
- alignes With op i e c 62443
- alignes With op i s o 24760
- supports op Identity Management
- has d bpedia resource dp identification (information)
Identity Managementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IdentityManagement
- belongs to
- Concern c
- has facts
- supports op Non-repudiation
- has d bpedia resource dp identity management
IDS Data Marketni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMDataMarket
- belongs to
- Standard Classification c
- has facts
- is Described in op IDS RAM
IDS Interoperabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMInteroperability
- belongs to
- Standard Classification c
- has facts
- is Described in op IDS RAM
IDS RAMni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMReferenceArchitectureModel
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- associated with op IIRA Functional Viewpoint
- has Publisher op IDSA
- alignes With op IIRA Functional Viewpoint
IDS RAM Business Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMBusinessLayer
- belongs to
- IDS RAM Layer c
- Standard Classification c
- has facts
- associated with op IIRA Business Domain
- associated with op Ocean Protocol System Viewpoint
- associated with op RAMI Business Layer
- associated with op x-road System Components
- is Described in op IDS RAM
- alignes With op IIRA Business Domain
- alignes With op Ocean Protocol System Viewpoint
- alignes With op RAMI Business Layer
- alignes With op x-road System Components
- frames op Role Categorization
IDS RAM Certification Perspectiveni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMCertification
- belongs to
- IDS RAM Perspective c
- Standard Classification c
- has facts
- is Described in op IDS RAM
- frames op Certification
- frames op Safety
- frames op Security
IDS RAM Functional Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMFunctionalLayer
- belongs to
- IDS RAM Layer c
- Standard Classification c
- has facts
- associated with op Data Sovereignty
- associated with op Interoperability
- is Described in op IDS RAM
IDS RAM Governance Perspectiveni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMGovernance
- belongs to
- IDS RAM Perspective c
- Standard Classification c
- has facts
- associated with op DTP Ecosystem
- associated with op DTP Security & Privacy
- associated with op IICF Framework Layer
- associated with op RAMI Business Layer
- is Described in op IDS RAM
- alignes With op DTP Ecosystem
- alignes With op DTP Security & Privacy
- alignes With op IICF Framework Layer
- alignes With op RAMI Business Layer
- frames op Compliance
- frames op Trustworthiness
IDS RAM Information Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMInformationLayer
- belongs to
- IDS RAM Layer c
- Standard Classification c
- has facts
- associated with op BDVA Data Management
- associated with op information domain
- associated with op IoT-A Information Viewpoint
- associated with op NGSI-LD Data Representation
- associated with op NGSI-LD Information Model
- associated with op RAMI Information Layer
- associated with op vocabulary
- is Described in op IDS RAM
- alignes With op BDVA Data Management
- alignes With op information domain
- alignes With op IoT-A Information Viewpoint
- alignes With op NGSI-LD Data Representation
- alignes With op NGSI-LD Information Model
- alignes With op RAMI Information Layer
- alignes With op vocabulary
IDS RAM Process Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMProcessLayer
- belongs to
- IDS RAM Layer c
- Standard Classification c
- has facts
- associated with op BDVA Data Analytics
- associated with op BDVA Data Management
- associated with op BDVA Data Processing Architectures
- associated with op DTP Deployment
- associated with op FIWARE Applications Services and Data Delivery
- associated with op IIRA Application Domain
- associated with op IIRA Operation Domain
- associated with op information domain
- associated with op FIWARE Interface to Networks and Devices
- associated with op IoT-A Functional Viewpoint
- associated with op IoT-A Information Viewpoint
- associated with op NGSI-LD API Operation
- associated with op Ocean Protocol System Viewpoint
- associated with op RAMI Functional Layer
- associated with op x-road Protocols and Interfaces
- associated with op x-road System Components
- is Described in op IDS RAM
- alignes With op BDVA Data Analytics
- alignes With op BDVA Data Management
- alignes With op BDVA Data Processing Architectures
- alignes With op DTP Deployment
- alignes With op FIWARE Applications Services and Data Delivery
- alignes With op IIRA Application Domain
- alignes With op IIRA Operation Domain
- alignes With op information domain
- alignes With op FIWARE Interface to Networks and Devices
- alignes With op IoT-A Functional Viewpoint
- alignes With op IoT-A Information Viewpoint
- alignes With op NGSI-LD API Operation
- alignes With op Ocean Protocol System Viewpoint
- alignes With op RAMI Functional Layer
- alignes With op x-road Protocols and Interfaces
- alignes With op x-road System Components
- frames op Service Choreography
- frames op Service Composition
- frames op Service Orchestration
IDS RAM Security Perspectiveni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMSecurity
- belongs to
- IDS RAM Perspective c
- Standard Classification c
- has facts
- associated with op BDVA Cybersecurity and Trust
- associated with op BDVA Data Protection
- associated with op FIWARE Security
- associated with op IIRA Security
- associated with op IIC Security Framework
- associated with op IoT-A Functional Viewpoint
- associated with op IoT-A Trust Security and Privacy
- associated with op r a m i
- is Described in op IDS RAM
- alignes With op BDVA Cybersecurity and Trust
- alignes With op BDVA Data Protection
- alignes With op FIWARE Security
- alignes With op IIRA Security
- alignes With op IIC Security Framework
- alignes With op IoT-A Functional Viewpoint
- alignes With op IoT-A Trust Security and Privacy
- alignes With op OCF Security
- frames op Authentication
- frames op authorization
- frames op communication
- frames op Data Access Control
- frames op Data Sovereignty
- frames op Data Usage Control
- frames op Identification
- frames op Identity Management
- frames op Privacy
- frames op Secure Communication
- frames op Security
- frames op Service Isolation
- frames op Trustworthiness
IDS RAM System Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSRAMSystemLayer
- belongs to
- IDS RAM Layer c
- Standard Classification c
- has facts
- associated with op DTP System
- associated with op Edgecross Edgecomputing Layer
- associated with op Edgecross IT Systems Layer
- associated with op FIWARE Architecture
- associated with op FIWARE Cloud Hosting
- associated with op FIWARE IoT Services Enablement
- associated with op IICF Framework Layer
- associated with op IIRA Control Domain
- associated with op IIRA Implementation Viewpoint
- associated with op IIRA Physical Systems
- associated with op FIWARE Interface to Networks and Devices
- associated with op IoT-A Deployment and Operation
- associated with op NGSI-LD API Operation
- associated with op NGSI-LD Architecture
- associated with op RAMI Communication Layer
- associated with op RAMI Integration Layer
- associated with op x-road Deplyoment View
- is Described in op IDS RAM
- alignes With op DTP System
- alignes With op Edgecross Edgecomputing Layer
- alignes With op Edgecross IT Systems Layer
- alignes With op FIWARE Architecture
- alignes With op FIWARE Cloud Hosting
- alignes With op FIWARE IoT Services Enablement
- alignes With op IICF Framework Layer
- alignes With op IIRA Control Domain
- alignes With op IIRA Physical Systems
- alignes With op FIWARE Interface to Networks and Devices
- alignes With op IoT-A Deployment and Operation
- alignes With op NGSI-LD API Operation
- alignes With op NGSI-LD Architecture
- alignes With op RAMI Communication Layer
- alignes With op RAMI Integration Layer
- alignes With op x-road Deplyoment View
IDS REFERENCE ARCHITECTURE MODEL INDUSTRIAL DATA SPACE VERSION 2.0ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDS_REFERENCE_ARCHITECTURE_MODEL_INDUSTRIAL_DATA_SPACE_VERSION_2_0
- belongs to
- oa specific resource c
IDS Trusted Connectorni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#TrustedConnector
- belongs to
- Technology c
- has facts
- associated with op d i n s p e c 27070
- associated with op IDS RAM
- alignes With op d i n s p e c 27070
- has official resource dp 1804.09442
IDSAni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IDSA
- belongs to
- organization c
- i io t consortium c
- has facts
- has official resource dp https://www.internationaldataspaces.org/en/
- has wikipedia article dp industrial data space association
IICni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIC
- belongs to
- organization c
- i io t consortium c
- StandardOrganization c
- has facts
- associated with op Industrial Internet Reference Architecture
- has official resource dp www-iiconsortium-org:
IIC Security Frameworkni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRASecurityFramework
- belongs to
- Standard Classification c
- has facts
- associated with op BDVA Cybersecurity and Trust
- associated with op BDVA Data Protection
- associated with op IDS RAM Security Perspective
- associated with op x-road System Components
- alignes With op BDVA Cybersecurity and Trust
- alignes With op BDVA Data Protection
- alignes With op IDS RAM Security Perspective
- alignes With op x-road System Components
- has official resource dp i i s f.htm
IIC Vocabularyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICVocabulary
- belongs to
- document c
- Publication
- Standard Classification c
- has facts
- associated with op IDS RAM Information Layer
- maker op IIC
- has Publisher op IIC
- is Described in op Industrial Internet Reference Architecture
- alignes With op IDS RAM Information Layer
IICFni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICF
- Is defined by
- https://www.iiconsortium.org/IICF.htm
- belongs to
- document c
- Publication
- has facts
- has Classification op IIRA Connectivity
IICFni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRC
- Is defined by
- https://www.iiconsortium.org/IICF.htm
- belongs to
- Standarization Framework c
iicf connectivity layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IicfConnectivityLayerAnno
- belongs to
- oa annotation c
IICF Framework Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFFrameworkLayer
- belongs to
- Connectivity Layer c
- Standard Classification c
- has facts
- associated with op d d s
- associated with op IDS RAM Governance Perspective
- associated with op IDS RAM System Layer
- associated with op i e c 62541
- associated with op one m2 m
- associated with op q1548249
- alignes With op IDS RAM Governance Perspective
- alignes With op IDS RAM System Layer
- frames op Authentication
- frames op communication
- frames op Data Access
- frames op Data Discovery
- frames op governance
- frames op Identification
- frames op Identity Management
- frames op Integrity Protection and Verification
- frames op Interoperability
- frames op Quality of Service
- frames op Secure Communication
- frames op Security
- frames op Semantic Interoperability
- frames op Service Description
- frames op Service Discovery
- frames op Syntactic Interoperability
- frames op Trustworthiness
IICF Link Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFLinkLayer
- belongs to
- Connectivity Layer c
- Standard Classification c
- has facts
- associated with op i e e e 802
- associated with op i e e e 802 16 2012
- associated with op wi fi
- frames op communication
IICF Network Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFNetworkLayer
- belongs to
- Connectivity Layer c
- Standard Classification c
- has facts
- associated with op IPv6
- frames op communication
- frames op IPv4 Support
- frames op IPv6 Support
- frames op Interoperability
- frames op Syntactic Interoperability
IICF Physical Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFPhysicalLayer
- belongs to
- Connectivity Layer c
- Standard Classification c
- has facts
- associated with op i e e e 802
- associated with op i e e e 802 16 2012
- frames op communication
IICF Transport Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IICFTansportLayer
- belongs to
- Connectivity Layer c
- Standard Classification c
- has facts
- associated with op h t t p
- associated with op h t t p2
- associated with op i e c 61158
- associated with op i s o 20922
- associated with op HTTP/1.1
- associated with op RFC 793
- associated with op CoAP
- associated with op u d p
- frames op cardinality of data sources
- frames op Cardinality of Participants
- frames op communication
- frames op Endpoint Invocation
- frames op Interoperability
- frames op Multilateralism
- frames op Secure Communication
- frames op Security
- frames op Service Composition
- frames op Syntactic Interoperability
- frames op Time Synchronization
- frames op Trustworthiness
- frames op Unicast
IIRA Application Domainni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAApplicationDomain
- belongs to
- IIRA Functional Domain c
- Standard Classification c
- has facts
- associated with op BDVA Cloud and High Performance Computing
- associated with op Edgecross IT Systems Layer
- associated with op FIWARE Advanced Web-based User Interface
- associated with op FIWARE Cloud Hosting
- associated with op IDS RAM Process Layer
- associated with op RAMI Functional Layer
- associated with op RAMI Information Layer
- is Described in op Industrial Internet Reference Architecture
- alignes With op BDVA Cloud and High Performance Computing
- alignes With op Edgecross IT Systems Layer
- alignes With op FIWARE Advanced Web-based User Interface
- alignes With op FIWARE Cloud Hosting
- alignes With op IDS RAM Process Layer
- alignes With op RAMI Functional Layer
- alignes With op RAMI Information Layer
- frames op bdva data viualisation and user interaction
- frames op Data Processing
- frames op Endpoint Invocation
- frames op Interoperability
- frames op Syntactic Interoperability
IIRA Business Domainni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRABusinessDomain
- belongs to
- IIRA Functional Domain c
- Standard Classification c
- has facts
- associated with op IDS RAM Business Layer
- associated with op Ocean Protocol System Viewpoint
- associated with op RAMI Business Layer
- is Described in op Industrial Internet Reference Architecture
- alignes With op IDS RAM Business Layer
- alignes With op Ocean Protocol System Viewpoint
- alignes With op RAMI Business Layer
- frames op process planning
IIRA Business Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRABusinessViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IVI Business Layer
- associated with op Ocean Protocol Business Viewpoint
- associated with op Ocean Protocol Marketplace Viewpoint
- is Described in op Industrial Internet Reference Architecture
- alignes With op IVI Business Layer
- alignes With op Ocean Protocol Business Viewpoint
- alignes With op Ocean Protocol Marketplace Viewpoint
- frames op Business Context
- frames op Business Value
- frames op Maintenance Cost
- frames op Product Liability
- frames op Resilience
- frames op Return On Investment
- frames op Safety
- frames op Security
- frames op Trustworthiness
IIRA Connectivityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAConnectivity
- belongs to
- IIRA Crosscutting Function c
- Standard Classification c
- has facts
- associated with op BDVA Data Processing Architectures
- associated with op Decision maker
- associated with op DTP System
- associated with op FIWARE Applications Services and Data Delivery
- associated with op i e c 62541
- associated with op IICF
- associated with op IoT-A Evolution and Interoperability
- associated with op link layer
- associated with op NGSI-LD API Operation
- associated with op RAMI Communication Layer
- associated with op REST
- associated with op one m2 m
- associated with op q1548249
- is Described in op Industrial Internet Reference Architecture
- alignes With op BDVA Data Processing Architectures
- alignes With op DTP System
- alignes With op FIWARE Applications Services and Data Delivery
- alignes With op IoT-A Evolution and Interoperability
- alignes With op NGSI-LD API Operation
- alignes With op RAMI Communication Layer
- frames op Authentication
- frames op cardinality of data sources
- frames op Cardinality of Participants
- frames op communication
- frames op Data Access
- frames op Data Discovery
- frames op Dynamic Adjustability
- frames op Endpoint Invocation
- frames op Evolvability
- frames op governance
- frames op IPv4 Support
- frames op IPv6 Support
- frames op Identification
- frames op Identity Management
- frames op Integrity Protection and Verification
- frames op Interoperability
- frames op Multilateralism
- frames op Network performance
- frames op Quality of Service
- frames op Reliability
- frames op Resilience
- frames op Safety
- frames op Scalability
- frames op Secure Communication
- frames op Security
- frames op Semantic Interoperability
- frames op Service Choreography
- frames op Service Composition
- frames op Service Deployment
- frames op Service Description
- frames op Service Discovery
- frames op Service life-cycle management
- frames op Service Orchestration
- frames op Syntactic Interoperability
- frames op Time Synchronization
- frames op Trustworthiness
- frames op Unicast
IIRA Control Domainni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAControlDomain
- belongs to
- IIRA Functional Domain c
- Standard Classification c
- has facts
- associated with op Edgecross Edgecomputing Layer
- associated with op FIWARE IoT Services Enablement
- associated with op IDS RAM System Layer
- associated with op IoT-A Information Viewpoint
- associated with op NGSI-LD API Operation
- associated with op RAMI Integration Layer
- associated with op x-road Protocols and Interfaces
- is Described in op Industrial Internet Reference Architecture
- alignes With op Edgecross Edgecomputing Layer
- alignes With op FIWARE IoT Services Enablement
- alignes With op IDS RAM System Layer
- alignes With op IoT-A Information Viewpoint
- alignes With op NGSI-LD API Operation
- alignes With op RAMI Integration Layer
- alignes With op x-road Protocols and Interfaces
- frames op Actuation
- frames op Asset Management
- frames op communication
- frames op Edge Analytics
- frames op IoT
- frames op Sensing
- frames op Virtual Entity
IIRA Distributed Data Managementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRADistributedDataManagement
- belongs to
- IIRA Crosscutting Function c
- Standard Classification c
- has facts
- associated with op FIWARE Cloud Hosting
- associated with op RAMI Communication Layer
- is Described in op Industrial Internet Reference Architecture
- alignes With op FIWARE Cloud Hosting
- alignes With op RAMI Communication Layer
- frames op Interoperability
- frames op Semantic Interoperability
IIRA Functional Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAFunctionalViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IDS RAM
- associated with op IoT-A Functional Viewpoint
- associated with op Ocean Protocol System Viewpoint
- is Described in op Industrial Internet Reference Architecture
- alignes With op IDS RAM
- alignes With op IoT-A Functional Viewpoint
- alignes With op Ocean Protocol System Viewpoint
- frames op process planning
- frames op Access Policy
- frames op Actuation
- frames op Authentication
- frames op authorization
- frames op Availability
- frames op bdva data viualisation and user interaction
- frames op cardinality of data sources
- frames op Cardinality of Participants
- frames op Cloud Computing Capability
- frames op communication
- frames op Data Access
- frames op Data Access Control
- frames op Data Analytics
- frames op Data at rest
- frames op Data Discovery
- frames op data in motion
- frames op Data Processing
- frames op Data Protection
- frames op Data Sovereignty
- frames op Dynamic Adjustability
- frames op Endpoint Invocation
- frames op Evolvability
- frames op governance
- frames op IPv4 Support
- frames op IPv6 Support
- frames op Identification
- frames op Identity Management
- frames op Integrity Protection and Verification
- frames op Interoperability
- frames op IoT
- frames op Multilateralism
- frames op Network performance
- frames op Privacy
- frames op Quality of Service
- frames op Real Time Analytics
- frames op Reliability
- frames op Resilience
- frames op Safety
- frames op Scalability
- frames op Secure Communication
- frames op Security
- frames op Security Configuration
- frames op Semantic Interoperability
- frames op Sensing
- frames op Service Access Control
- frames op Service Choreography
- frames op Service Composition
- frames op Service Deployment
- frames op Service Description
- frames op Service Discovery
- frames op Service Isolation
- frames op Service level agreement
- frames op Service life-cycle management
- frames op Service Orchestration
- frames op Stream processing
- frames op Syntactic Interoperability
- frames op Time Synchronization
- frames op Trustworthiness
- frames op Unicast
IIRA Implementation Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAImplementationViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op control domain
- associated with op DTP Deployment
- associated with op FIWARE Architecture
- associated with op IDS RAM System Layer
- associated with op IIRA Application Domain
- associated with op IIRA Business Domain
- associated with op IIRA Operation Domain
- associated with op information domain
- associated with op IoT-A Deployment and Operation
- associated with op NGSI-LD Architecture
- associated with op x-road Deplyoment View
- is Described in op Industrial Internet Reference Architecture
- alignes With op DTP Deployment
- alignes With op FIWARE Architecture
- alignes With op IoT-A Deployment and Operation
- alignes With op NGSI-LD Architecture
- alignes With op x-road Deplyoment View
- frames op Cloud Computing Capability
- frames op communication
- frames op Data Processing
- frames op Edge computing
- frames op Endpoint Description
- frames op Interoperability
- frames op Semantic Interoperability
IIRA Information Domainni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAInformationDomain
- belongs to
- IIRA Functional Domain c
- Standard Classification c
- has facts
- associated with op BDVA Data Analytics
- associated with op BDVA Data Processing Architectures
- associated with op DTP System
- associated with op Edgecross Edgecomputing Layer
- associated with op IDS RAM Information Layer
- associated with op IDS RAM Process Layer
- associated with op IoT-A Information Viewpoint
- associated with op NGSI-LD Information Model
- associated with op RAMI Information Layer
- is Described in op Industrial Internet Reference Architecture
- alignes With op BDVA Data Analytics
- alignes With op BDVA Data Processing Architectures
- alignes With op DTP System
- alignes With op Edgecross Edgecomputing Layer
- alignes With op IDS RAM Information Layer
- alignes With op IDS RAM Process Layer
- alignes With op IoT-A Information Viewpoint
- alignes With op NGSI-LD Information Model
- alignes With op RAMI Information Layer
- frames op Data Analytics
- frames op Data Processing
- frames op Interoperability
- frames op Semantic Interoperability
- frames op Stream processing
- frames op Syntactic Interoperability
IIRA Intelligent and Resilient Controlni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAIntelligentAndResilientControl
- belongs to
- IIRA Crosscutting Function c
- Standard Classification c
- has facts
- is Described in op Industrial Internet Reference Architecture
IIRA Operation Domainni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAOperationsDomain
- belongs to
- IIRA Functional Domain c
- Standard Classification c
- has facts
- associated with op DTP System
- associated with op Edgecross Edgecomputing Layer
- associated with op IDS RAM Process Layer
- associated with op IoT-A Information Viewpoint
- associated with op IVI Activity View
- associated with op RAMI Functional Layer
- is Described in op Industrial Internet Reference Architecture
- alignes With op DTP System
- alignes With op Edgecross Edgecomputing Layer
- alignes With op IDS RAM Process Layer
- alignes With op IoT-A Information Viewpoint
- alignes With op IVI Activity View
- alignes With op RAMI Functional Layer
- frames op Data Analytics
- frames op Real Time Analytics
- frames op Service Deployment
- frames op Service life-cycle management
IIRA Physical Systemsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAPhysicalSystems
- belongs to
- Standard Classification c
- has facts
- associated with op Edgecross FA
- associated with op IDS RAM System Layer
- associated with op IVI Asset View
- associated with op RAMI Asset Layer
- is Described in op Industrial Internet Reference Architecture
- alignes With op Edgecross FA
- alignes With op IDS RAM System Layer
- alignes With op IVI Asset View
- alignes With op RAMI Asset Layer
- has official resource dp i i r a.htm
IIRA Privacyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAPrivacy
- belongs to
- IIRA System Characteristic c
- Standard Classification c
- has facts
- associated with op DTP Security & Privacy
- is Described in op Industrial Internet Reference Architecture
- alignes With op DTP Security & Privacy
- frames op Data Sovereignty
- frames op Privacy
- frames op Trustworthiness
IIRA Reliabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAReliability
- belongs to
- IIRA System Characteristic c
- Standard Classification c
- has facts
- is Described in op Industrial Internet Reference Architecture
- frames op Reliability
- frames op Trustworthiness
IIRA Resilienceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAResilience
- belongs to
- IIRA System Characteristic c
- Standard Classification c
- has facts
- is Described in op Industrial Internet Reference Architecture
IIRA Safetyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRASafety
- belongs to
- IIRA System Characteristic c
- Standard Classification c
- has facts
- is Described in op Industrial Internet Reference Architecture
IIRA Scalabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAScalability
- belongs to
- IIRA System Characteristic c
- Standard Classification c
- has facts
- associated with op FIWARE Cloud Hosting
- is Described in op Industrial Internet Reference Architecture
- alignes With op FIWARE Cloud Hosting
- frames op Scalability
IIRA Securityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRASecurity
- belongs to
- IIRA System Characteristic c
- Standard Classification c
- has facts
- associated with op data owner
- associated with op Decision maker
- associated with op DTP Security & Privacy
- associated with op FIWARE Security
- associated with op IDS RAM Security Perspective
- associated with op IoT-A Availability and Resilience
- associated with op IoT-A Trust Security and Privacy
- associated with op q1548249
- is Described in op Industrial Internet Reference Architecture
- alignes With op DTP Security & Privacy
- alignes With op FIWARE Security
- alignes With op IDS RAM Security Perspective
- alignes With op IoT-A Availability and Resilience
- alignes With op IoT-A Trust Security and Privacy
- frames op Access Policy
- frames op authorization
- frames op Availability
- frames op Cloud Computing Capability
- frames op communication
- frames op Data Access Control
- frames op Data at rest
- frames op data in motion
- frames op Data Processing
- frames op Data Protection
- frames op Data Sovereignty
- frames op Identification
- frames op Identity Management
- frames op Integrity Protection and Verification
- frames op Privacy
- frames op Reliability
- frames op Resilience
- frames op Safety
- frames op Secure Communication
- frames op Security
- frames op Security Configuration
- frames op Service Access Control
- frames op Service Isolation
- frames op Service level agreement
- frames op Service life-cycle management
- frames op Trustworthiness
IIRA Usage Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRAUsageViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op bdva data viualisation and user interaction
- associated with op DTP Ecosystem
- associated with op FIWARE Advanced Web-based User Interface
- associated with op IVI Management View
- is Described in op Industrial Internet Reference Architecture
- alignes With op bdva data viualisation and user interaction
- alignes With op DTP Ecosystem
- alignes With op FIWARE Advanced Web-based User Interface
- alignes With op IVI Management View
- frames op process planning
- frames op Dynamic Adjustability
- frames op Evolvability
- frames op Role Categorization
- frames op Service Choreography
- frames op Service Composition
- frames op Service Deployment
- frames op Service life-cycle management
- frames op Service Orchestration
industrial data spaceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IndustrialDataSpace
- belongs to
- Standarization Framework c
Industrial Internet Architecture Version 1ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Industrial_Internet_Architecture_Version_1
- belongs to
- oa specific resource c
Industrial Internet Architecture Version 1ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#The_Industrial_Internet_of_Things_Volume_G1_Reference_Architecture
- belongs to
- oa specific resource c
Industrial Internet of Things Volume G4: Security Frameworkni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Industrial_Internet_of_Things_Volume_G4_Security_Framework
- belongs to
- oa specific resource c
Industrial Internet Reference Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIRA
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- has Publisher op IIC
- has official resource dp i i r a.htm
- has Target Concern op end user
- has Target Concern op Business Value
- has Target Concern op Decision maker
- has Target Concern op developer
- has Target Concern op Maintenance Cost
- has Target Concern op Product Liability
- has Target Concern op Product Manager
- has Target Concern op Return On Investment
- has Target Concern op System Engineer
- has Target Concern op system operator
- has Target Concern op q1548249
Industrial Value Chain Reference Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IVRA
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- associated with op IVI
- has official resource dp doc 161208 industrial value chain reference architecture.pdf
Industrial Value Chain Reference Architecture (IVRA)ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Industrial_Value_Chain_Reference_Architecture_IVRA
- belongs to
- oa specific resource c
Industrial Value Chain Reference Architecture (IVRA)- Nextni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Industrial_Value_Chain_Reference_Architecture_IVRA_Next
- belongs to
- oa specific resource c
Information Privacyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Information_Privacy
Information Securityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#InformationSecurity
Integrity Protection and Verificationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IntegrityProtection
- belongs to
- Concern c
- has facts
- supports op Device Security
- has d bpedia resource dp system integrity
interface networks devices annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#InterfaceNetworksDevicesAnno
- belongs to
- oa annotation c
Interoperabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Interoperability
- belongs to
- Concern c
- has facts
- has d bpedia resource dp interoperability
Introduction of X-teeni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#introductionXtee
- belongs to
- document c
- Publication
- Technical Report c
- has facts
- maker op estonian information system authority
- has Classification op x-road Deplyoment View
- has Classification op x-road Protocols and Interfaces
- has Classification op x-road System Components
- has Classification op x-road Technology Matrix
- has Publisher op estonian information system authority
- has official resource dp introduction x tee.html
IoTni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IoT
- belongs to
- Concern c
- has facts
- has d bpedia resource dp internet of things
IoT-Ani back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IoTA
- belongs to
- organization c
- i io t consortium c
- has facts
- associated with op IoT-A Reference Architecture
IoT-A Availability and Resilienceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaAvailabilityResilience
- belongs to
- IoT-A Perspective c
- Standard Classification c
- has facts
- associated with op Security
- is Described in op IoT-A Reference Architecture
- alignes With op Security
- frames op Availability
- frames op Resilience
- frames op Security
- frames op Trustworthiness
IoT-A Deployment and Operationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaDeploymentOperationViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IDS RAM System Layer
- associated with op IIRA Implementation Viewpoint
- is Described in op IoT-A Reference Architecture
- alignes With op IDS RAM System Layer
- alignes With op IIRA Implementation Viewpoint
- frames op energy efficiency
- frames op Dynamic Adjustability
- frames op Evolvability
- frames op Service Choreography
- frames op Service Composition
- frames op Service Deployment
- frames op Service life-cycle management
- frames op Service Orchestration
IoT-A Evolution and Interoperabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaEvolutionInteroperability
- belongs to
- IoT-A Perspective c
- Standard Classification c
- has facts
- associated with op IIRA Connectivity
- associated with op RAMI Integration Layer
- is Described in op IoT-A Reference Architecture
- alignes With op IIRA Connectivity
- alignes With op RAMI Integration Layer
- frames op Dynamic Adjustability
- frames op Evolvability
- frames op Interoperability
- frames op Service Choreography
- frames op Service Composition
- frames op Service Orchestration
IoT-A Functional Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaFunctionalViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IDS RAM Process Layer
- associated with op IDS RAM Security Perspective
- associated with op IIRA Functional Viewpoint
- associated with op RAMI Asset Layer
- associated with op r a m i functional
- is Described in op IoT-A Reference Architecture
- alignes With op IDS RAM Process Layer
- alignes With op IDS RAM Security Perspective
- alignes With op IIRA Functional Viewpoint
- alignes With op RAMI Asset Layer
- alignes With op RAMI Functional Layer
- frames op configuration
- frames op process planning
- frames op Authentication
- frames op authorization
- frames op communication
- frames op Data Sovereignty
- frames op Identity Management
- frames op Privacy
- frames op Security
- frames op Service Choreography
- frames op Service Composition
- frames op Service Orchestration
- frames op Thing representation
- frames op Trustworthiness
- frames op Virtual Entity
IoT-A Information Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaInformationViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IDS RAM Information Layer
- associated with op IDS RAM Process Layer
- associated with op IIRA Control Domain
- associated with op IIRA Operation Domain
- associated with op information domain
- associated with op RAMI Communication Layer
- is Described in op IoT-A Reference Architecture
- alignes With op IDS RAM Information Layer
- alignes With op IDS RAM Process Layer
- alignes With op IIRA Control Domain
- alignes With op IIRA Operation Domain
- alignes With op information domain
- alignes With op RAMI Communication Layer
- frames op communication
- frames op Data Analytics
- frames op Data at rest
- frames op data in motion
- frames op Data lifecycle management
- frames op Endpoint Invocation
- frames op Interoperability
- frames op Semantic Interoperability
- frames op Service Description
- frames op Syntactic Interoperability
- frames op Thing representation
- frames op Virtual Entity
- has official resource dp 978 3 642 40403 0
IoT-A Performance and Scalabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaPerformanceScalability
- belongs to
- IoT-A Perspective c
- Standard Classification c
- has facts
- is Described in op IoT-A Reference Architecture
- frames op communication
- frames op Interoperability
- frames op Network performance
- frames op Quality of Service
- frames op Scalability
- frames op Semantic Interoperability
- frames op Service Description
IoT-A Reference Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaReferenceArchitecture
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- has Publisher op IoT-A
IoT-A Trust Security and Privacyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaTrustSecurityPrivacy
- belongs to
- IoT-A Perspective c
- Standard Classification c
- has facts
- associated with op IDS RAM Security Perspective
- associated with op IIRA Security
- is Described in op IoT-A Reference Architecture
- alignes With op IDS RAM Security Perspective
- alignes With op Security
- frames op Data Sovereignty
- frames op Privacy
- frames op Security
- frames op Trustworthiness
iota availability resilience annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaAvailabilityResilienceAnno
- belongs to
- oa annotation c
iota deployment operation viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaDeploymentOperationViewpointAnno
- belongs to
- oa annotation c
iota evolution interoperability annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaEvolutionInteroperabilityAnno
- belongs to
- oa annotation c
iota functional viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaFunctionalViewpointAnno
- belongs to
- oa annotation c
iota information viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaInformationViewpointAnno
- belongs to
- oa annotation c
iota performance scalability annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaPerformanceScalabilityAnno
- belongs to
- oa annotation c
iota perspective annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaPerspectiveAnno
- belongs to
- oa annotation c
iota reference architecture annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaReferenceArchitectureAnno
- belongs to
- oa annotation c
iota trust security privacy annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IotaTrustSecurityPrivacyAnno
- belongs to
- oa annotation c
IoTivityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IoTivity
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp https://www.iotivity.org/
IPSOni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IPSO
- belongs to
- organization c
- i io t consortium c
- has facts
- has official resource dp http://www.ipso-alliance.org/
IPSO App Frameworkni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IpsoAppFramework
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp draft ipso app framework 04.pdf
IPv4 Supportni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IPv4Support
- belongs to
- Concern c
- has facts
- supports op Syntactic Interoperability
- has d bpedia resource dp internet protocol
IPv6ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IPv6
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has wikipedia article dp i pv6
- has Target Concern op Syntactic Interoperability
IPv6 Supportni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IPv6Support
- belongs to
- Concern c
- has facts
- supports op Syntactic Interoperability
- has d bpedia resource dp internet protocol
ISO 50001ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ISO_50001
- belongs to
- Standard c
- has facts
- has Target Concern op energy management
ISO 9000ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ISO_9000
- belongs to
- Standard c
- has facts
- has Classification op cross level
- has Classification op IDS RAM Certification Perspective
- has Target Concern op Quality of Service
ISO/IEC 29115ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ISO_29115
- belongs to
- Standard c
- has facts
- has Target Concern op Authentication
- has Target Concern op Identification
ISO/IEC 9594ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ISO_9594
- belongs to
- Standard c
- has facts
- has Classification op Data Sovereignty
- has Classification op IDS RAM Certification Perspective
- has Classification op IDS RAM Security Perspective
ISO/IEC 9594-8ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ISO_9594-8
- belongs to
- Standard c
- has facts
- has Classification op Data Sovereignty
- has Classification op IDS RAM Certification Perspective
- has Classification op IDS RAM Security Perspective
Isolationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ProcessIsolation
- belongs to
- Concern c
- has facts
- supports op Integrity Protection and Verification
- has wikipedia article dp process isolation
IVIni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Ivi
- belongs to
- organization c
- i io t consortium c
- has facts
- has official resource dp https://iv-i.org/
IVI Activity Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviActivityLayer
- belongs to
- IVI Layer c
- Standard Classification c
- has facts
- associated with op engineering
- associated with op manufacturing
- is Described in op Industrial Value Chain Reference Architecture
- alignes With op engineering
- alignes With op manufacturing
- frames op process planning
ivi activity layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviActivityLayerAnno
- belongs to
- oa annotation c
IVI Activity Viewni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviActivityView
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op engineering
- associated with op IIRA Operation Domain
- is Described in op Industrial Value Chain Reference Architecture
- alignes With op engineering
- alignes With op IIRA Operation Domain
- frames op manufacturing
ivi activity view annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviActivityViewAnno
- belongs to
- oa annotation c
IVI Asset Viewni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviAssetView
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IIRA Physical Systems
- associated with op RAMI Asset Layer
- is Described in op Industrial Value Chain Reference Architecture
- alignes With op IIRA Physical Systems
- alignes With op RAMI Asset Layer
- frames op Thing representation
ivi asset view annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviAssetViewAnno
- belongs to
- oa annotation c
IVI Business Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviBusinessLayer
- belongs to
- IVI Layer c
- Standard Classification c
- has facts
- associated with op IIRA Business Viewpoint
- associated with op RAMI Business Layer
- is Described in op Industrial Value Chain Reference Architecture
- alignes With op IIRA Business Viewpoint
- alignes With op RAMI Business Layer
- frames op Business Context
- frames op Business Transactions
ivi business layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviBusinessLayerAnno
- belongs to
- oa annotation c
IVI Management Viewni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviManagementView
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IIRA Usage Viewpoint
- associated with op RAMI Functional Layer
- is Described in op Industrial Value Chain Reference Architecture
- alignes With op IIRA Usage Viewpoint
- alignes With op RAMI Functional Layer
- frames op Business Context
- frames op Business Transactions
- frames op Maintenance Cost
- frames op Quality of Service
- frames op Service level agreement
- frames op Service life-cycle management
ivi management view annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviManagementViewAnno
- belongs to
- oa annotation c
IVI Specification Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviSpecificationLayer
- belongs to
- IVI Layer c
- Standard Classification c
- has facts
- associated with op engineering
- associated with op type development
- is Described in op Industrial Value Chain Reference Architecture
- alignes With op engineering
- alignes With op type development
- frames op Data Processing
ivi specification layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IviSpecificationLayerAnno
- belongs to
- oa annotation c
JMSni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#JMS
- belongs to
- document c
- Publication
- Technical Specification c
JSON Web Tokenni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_7519
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op i e t f
- has Classification op Data Sovereignty
- has Classification op IDS RAM Security Perspective
- has Publisher op i e t f
- has official resource dp rfc7519
Jurisdictional Issuesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Jurisdictional_Issues
- belongs to
- Concern c
- has facts
- supports op Cloud Computing Capability
- has wikipedia article dp jurisdiction
key rockni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#KeyRock
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- associated with op FIWARE Data/Context Management
- associated with op FIWARE Security
- has Target Concern op Identity Management
LatencyReductionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#LatencyReduction
- belongs to
- Concern c
- has facts
- supports op communication
- has wikipedia article dp latency (engineering)
LDAPni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_4511
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- maker op i e t f
- has Developer op i e t f
- has Publisher op i e t f
- has official resource dp rfc4511
- has wikipedia article dp lightweight directory access protocol
- has Target Concern op Cross-domain Identity Management
Lightweight M2M v1.0ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OMALightweightM2M
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp lightweight m2 m v1 0.aspx
Local Data Confidentialityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#LocalDataConfidentiality
- belongs to
- Concern c
Loggingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Logging
- belongs to
- Concern c
- has facts
- supports op Data Usage Control
- supports op Service Access Control
- has d bpedia resource dp data logger
Long Term Business Sustainabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Long_Term_Business_Sustainability
- belongs to
- Concern c
- has facts
- supports op Business Context
- has wikipedia article dp sustainability
low power wi fini back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#LowPowerWiFi
- belongs to
- document c
- Publication
- Technical Specification c
Machine Learningni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#MachineLearning
- belongs to
- Concern c
- has facts
- supports op Artificial Intelligence
- has d bpedia resource dp machine learning
Maintenance Costni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#MaintenanceCost
- belongs to
- Concern c
- has facts
- supports op Business Context
Message precedenceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#MessagePriority
- belongs to
- Concern c
- has facts
- supports op communication
- has d bpedia resource dp message precedence
Mobil Devicesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#MobilDevices
Muhammad Usmanni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#MuhammadUsman
- belongs to
- person c
Multilateralismni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Multilaterism
- belongs to
- Concern c
- has facts
- supports op cardinality of data sources
Multiple Identitiesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#MultipleIdentities
- belongs to
- Concern c
- has facts
- supports op Identity Management
Network performanceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#NetworkPerformance
- belongs to
- Concern c
- has facts
- supports op communication
- supports op Quality of Service
- has d bpedia resource dp network performance
network securityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#NetworkSecurity
Network Virtualizationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#NetworkVirtualization
- belongs to
- Concern c
- has facts
- supports op communication
- has wikipedia article dp network virtualization
NGSIni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#NGSI
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- maker op FIWARE Architecture
- has Publisher op FIWARE Architecture
- has official resource dp http://fiware.github.io/specifications/ngsiv2/stable/
NGSI-LD API Operationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#NgsiLdApiOperation
- belongs to
- NGSI Context Information Management API c
- Standard Classification c
- has facts
- associated with op FIWARE Data/Context Management
- associated with op IDS RAM Process Layer
- associated with op IDS RAM System Layer
- associated with op IIRA Connectivity
- associated with op IIRA Control Domain
- is Described in op FIWARE Architecture
- alignes With op FIWARE Data/Context Management
- alignes With op IDS RAM Process Layer
- alignes With op IDS RAM System Layer
- alignes With op IIRA Connectivity
- alignes With op IIRA Control Domain
- frames op communication
- frames op Endpoint Invocation
- frames op Interoperability
- frames op Syntactic Interoperability
NGSI-LD Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#NgsiLdArchitecture
- belongs to
- NGSI Context Information Management API c
- Standard Classification c
- has facts
- associated with op FIWARE Applications Services and Data Delivery
- associated with op FIWARE Cloud Hosting
- associated with op IDS RAM System Layer
- associated with op IIRA Implementation Viewpoint
- associated with op FIWARE Interface to Networks and Devices
- associated with op RAMI Integration Layer
- is Described in op FIWARE Architecture
- alignes With op FIWARE Applications Services and Data Delivery
- alignes With op FIWARE Cloud Hosting
- alignes With op IDS RAM System Layer
- alignes With op IIRA Implementation Viewpoint
- alignes With op FIWARE Interface to Networks and Devices
- alignes With op RAMI Integration Layer
- frames op process planning
- frames op Interoperability
- frames op Syntactic Interoperability
NGSI-LD Data Representationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#NgsiLdDataRepresentation
- belongs to
- NGSI Context Information Management API c
- Standard Classification c
- has facts
- associated with op FIWARE Data/Context Management
- associated with op IDS RAM Information Layer
- associated with op RAMI Functional Layer
- associated with op r d f
- is Described in op FIWARE Architecture
- alignes With op FIWARE Data/Context Management
- alignes With op IDS RAM Information Layer
- alignes With op RAMI Functional Layer
- frames op Data Description
- frames op Interoperability
- frames op Semantic Interoperability
NGSI-LD Information Modelni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#NgsiLdInformationModel
- belongs to
- NGSI Context Information Management API c
- Standard Classification c
- has facts
- associated with op FIWARE Data/Context Management
- associated with op IDS RAM Information Layer
- associated with op information domain
- associated with op RAMI Information Layer
- is Described in op FIWARE Architecture
- alignes With op FIWARE Data/Context Management
- alignes With op IDS RAM Information Layer
- alignes With op information domain
- alignes With op RAMI Information Layer
- frames op Data Analytics
- frames op Data Description
- frames op Geospatial data and information
- frames op Interoperability
- frames op Semantic Interoperability
Non-repudiationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#NonRepudiation
- belongs to
- Concern c
- has facts
- supports op Integrity Protection and Verification
- has d bpedia resource dp non repudiation
- has wikipedia article dp non repudiation
o f r a agility pillar annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAAgilityPillarAnno
- belongs to
- oa annotation c
o f r a autonomy pillar annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAAutonomyPillarAnno
- belongs to
- oa annotation c
o f r a data analytics and control perspective annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRADataAnalyticsAndControlPerspectiveAnno
- belongs to
- oa annotation c
o f r a deployment viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRADeploymentViewpointAnno
- belongs to
- oa annotation c
o f r a functional viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAFunctionalViewpointAnno
- belongs to
- oa annotation c
o f r a hierarchy pillar annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAHierarchyPillarAnno
- belongs to
- oa annotation c
o f r a it business and cross fog applications perspective annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAItBusinessAndCrossFogApplicationsPerspectiveAnno
- belongs to
- oa annotation c
o f r a manageability perspective annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAManageabilityPerspectiveAnno
- belongs to
- oa annotation c
o f r a node view annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRANodeViewAnno
- belongs to
- oa annotation c
o f r a openness pillar annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAOpennessPillarAnno
- belongs to
- oa annotation c
o f r a performance perspective annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAPerformancePerspectiveAnno
- belongs to
- oa annotation c
o f r a programmability pillar annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAProgrammabilityPillarAnno
- belongs to
- oa annotation c
o f r a r a s pillar annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRA_RASPillarAnno
- belongs to
- oa annotation c
o f r a scalability pillar annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAScalabilityPillarAnno
- belongs to
- oa annotation c
o f r a security perspective annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRASecurityPerspectiveAnno
- belongs to
- oa annotation c
o f r a security pillar annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRASecurityPillarAnno
- belongs to
- oa annotation c
o f r a software viewni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRASoftwareView
- belongs to
- Viewpoint c
- has facts
- alignes With op IIRA Application Domain
- frames op Service Discovery
o f r a software view annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRASoftwareViewAnno
- belongs to
- oa annotation c
o f r a system view annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRASystemViewAnno
- belongs to
- oa annotation c
Objects Safety and Securityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Objects_Safety_and_security
ocean business viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OceanBusinessViewpointAnno
- belongs to
- oa annotation c
ocean marketplace viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OceanMarketplaceViewpointAnno
- belongs to
- oa annotation c
Ocean Protocolni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OceanProtocol
- belongs to
- document c
- Publication
- Standarization Framework c
- Technical Specification c
- has facts
- maker op Ocean Protocol Foundation
- has Developer op Ocean Protocol Foundation
- has Publisher op Ocean Protocol Foundation
- has official resource dp oceanprotocol-com:
Ocean Protocol Business Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OceanBusinessViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IIRA Business Viewpoint
- is Described in op Ocean Protocol
- alignes With op IIRA Business Viewpoint
- frames op Business Context
- frames op Business Transactions
- frames op Role Categorization
- frames op Trustworthiness
Ocean Protocol Foundationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OceanProtocolFoundation
- belongs to
- organization c
- StandardOrganization c
- has facts
- has official resource dp oceanprotocol-com:
Ocean Protocol Marketplace Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OceanMarketplaceViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op IIRA Business Viewpoint
- is Described in op Ocean Protocol
- alignes With op IIRA Business Viewpoint
- frames op Business Context
Ocean Protocol System Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OceanSystemViewpoint
- belongs to
- Standard Classification c
- Viewpoint c
- has facts
- associated with op data consumer
- associated with op data provider
- associated with op IDS RAM Business Layer
- associated with op IDS RAM Process Layer
- associated with op IIRA Business Domain
- associated with op IIRA Functional Viewpoint
- associated with op RAMI Functional Layer
- is Described in op Ocean Protocol
- alignes With op IDS RAM Business Layer
- alignes With op IDS RAM Process Layer
- alignes With op IIRA Business Domain
- alignes With op IIRA Functional Viewpoint
- alignes With op RAMI Functional Layer
- frames op Artificial Intelligence
- frames op authorization
- frames op Availability
- frames op Business Context
- frames op Business Transactions
- frames op Data Access
- frames op Data Access Control
- frames op Data Analytics
- frames op Data Discovery
- frames op Data Sovereignty
- frames op governance
- frames op Identification
- frames op Identity Management
- frames op Integrity Protection and Verification
- frames op Interoperability
- frames op Privacy
- frames op Provenance Tracking
- frames op Security
- frames op Service level agreement
- frames op Service life-cycle management
- frames op Syntactic Interoperability
- frames op Trustworthiness
Ocean Protocol: A Decentralized Data Exchange Protocol to Unlock Data for Artificial Intelligence. Reference Marketplace Framework. Feb 2019ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Ocean_Protocol_Reference_Marketplace_Framework_Feb_2019
- belongs to
- oa specific resource c
Ocean Protocol: A Decentralized Data Exchange Protocol,powered by blockchain technology and a cryptotoken. Business Strategy. Oct 2017ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Ocean_Protocol_Business_Strategy_Oct_2017
- belongs to
- oa specific resource c
Ocean Protocol: A Decentralized Substrate for AI Data & Services . Technical Whitepaper. Apr 2019ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Ocean_Protocol_Technical_Whitepaper_Apr_2019
- belongs to
- oa specific resource c
ocean system viewpoint annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OceanSystemViewpointAnno
- belongs to
- oa annotation c
OCF Core Frameworkni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfCoreFramework
- belongs to
- OCF Framework Block c
- has facts
- is Described in op OCF Framework
- frames op communication
- frames op Endpoint Invocation
- frames op Identification
- frames op Service Discovery
- frames op Syntactic Interoperability
ocf core framework annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfCoreFrameworkAnno
- belongs to
- oa annotation c
OCF Data Modelsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfDataModels
- belongs to
- OCF Framework Block c
- has facts
- is Described in op OCF Framework
- frames op Semantic Interoperability
ocf data models annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfDataModelsAnno
- belongs to
- oa annotation c
OCF Frameworkni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfFramework
- belongs to
- Standarization Framework c
- has facts
- has Publisher op Open Connectivity Foundation
ocf framework annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfFrameworkAnno
- belongs to
- oa annotation c
OCF L2 Connectivityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfL2Connectivity
- belongs to
- OCF Framework Block c
- has facts
- is Described in op OCF Framework
- frames op Connectivity
- frames op Syntactic Interoperability
ocf l2 connectivity annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfL2ConnectivityAnno
- belongs to
- oa annotation c
OCF Networkingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfNetworking
- belongs to
- OCF Framework Block c
- has facts
- associated with op IPv6
- is Described in op OCF Framework
- frames op Connectivity
- frames op IPv6 Support
ocf networking annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfNetworkingAnno
- belongs to
- oa annotation c
OCF Securityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfSecurity
- belongs to
- OCF Framework Block c
- has facts
- associated with op RAML
- has Publisher op Open Connectivity Foundation
- is Described in op OCF Framework
- alignes With op security
- alignes With op BDVA Cybersecurity and Trust
- alignes With op FIWARE Security
- alignes With op IDS RAM Security Perspective
- alignes With op IIRA Security
- alignes With op IIC Security Framework
- alignes With op IoT-A Trust Security and Privacy
- alignes With op open fog security perspective
- frames op Certification
- frames op Connectivity
- frames op Secure Communication
ocf security annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OcfSecurityAnno
- belongs to
- oa annotation c
ODRLni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ODRL
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op w3 c
- has Classification op IDS RAM Information Layer
- has Classification op IDS RAM Security Perspective
- has Publisher op w3 c
- has official resource dp https://www.w3.org/TR/odrl-model/
OMG DDSni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OMG_DDS
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op o m g
- has Classification op IICF Framework Layer
- has Classification op IIRA Connectivity
- has Publisher op o m g
- related To op i e c 29182 1
- related To op i e c 61158
- related To op i e c 61784
- related To op OMG DDS
- has tag dp "Data Distribution Service for real-time systems"@en
- has d bpedia resource dp data distribution service
- has official resource dp http://portals.omg.org/dds/
- has wikipedia article dp data distribution service
Open Connectivity Foundationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OpenConnectivityFoundation
- belongs to
- StandardOrganization c
- has facts
- has d bpedia resource dp open connectivity foundation
Open Mobile Allianceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OMA
- belongs to
- organization c
- i io t consortium c
- has facts
- has official resource dp http://openmobilealliance.org/about-oma/work-program/m2m-enablers/
OpenAPIni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OpenApi
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has d bpedia resource dp open a p i specification
OpenFog Agility Pillarni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAAgilityPillar
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op agility
OpenFog Architecture Whitepaperni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OpenFogArchitecture
- belongs to
- Publication
- has facts
- has Publisher op OpenFog Consortium
- has d bpedia resource dp open fog consortium
- has official resource dp https://www.openfogconsortium.org/white-paper-reference-architecture/white-paper-download-open-fog-reference-architecture/
OpenFog AutonomyPillarni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAAutonomyPillar
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op Autonomous Communication
- frames op Autonomous Configuration
OpenFog Consortiumni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OpenFogConsortium
- belongs to
- i io t consortium c
- has facts
- has official resource dp https://www.openfogconsortium.org/
OpenFog Data Analytics and Control Perspectiveni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRADataAnalyticsAndControlPerspective
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- alignes With op IIRA Control Domain
- alignes With op information domain
- frames op Data Analytics
OpenFog Deployment Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRADeploymentViewpoint
- belongs to
- Viewpoint c
- has facts
- is Described in op OpenFog Reference Architecture
- alignes With op IIRA Implementation Viewpoint
- frames op Service Deployment
OpenFog Functional Viewpointni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAFunctionalViewpoint
- belongs to
- Viewpoint c
- has facts
- is Described in op OpenFog Reference Architecture
OpenFog Hierarchy Pillarni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAHierarchyPillar
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op Business Value
- frames op Data Analytics
- frames op Sensing
OpenFog IT Business and Cross-fog Applications Perspectiveni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAItBusinessAndCrossFogApplicationsPerspective
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op Business Context
OpenFog Manageability Perspectiveni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAManageabilityPerspective
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op Autonomous Configuration
- frames op Service life-cycle management
OpenFog Node Viewni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRANodeView
- belongs to
- Viewpoint c
- has facts
- associated with op wi fi
- is Described in op OpenFog Reference Architecture
- alignes With op IDS RAM System Layer
- alignes With op IIRA Physical Systems
- alignes With op RAMI Asset Layer
- frames op Data Storage
- frames op Network performance
- frames op Physical Connectivity
- frames op Security
OpenFog Opennes Pillarni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAOpennessPillar
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op Interoperability
- frames op Service Composition
OpenFog Programmability Pillarni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAProgrammabilityPillar
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op Programmability
OpenFog RAS Pillarni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRA_RASPillar
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op Availability
- frames op Maintenance Cost
- frames op Reliability
OpenFog Reference Architectureni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OpenFogReferenceArchitecture
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- has Publisher op OpenFog Consortium
- has official resource dp https://www.openfogconsortium.org/ra/
OpenFog Reference Architecture for Fog Computingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OpenFog_Reference_Architecture_for_Fog_Computing
- belongs to
- oa specific resource c
OpenFog Scalability Pillarni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAScalabilityPillar
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op Scalability
OpenFog Security Perspectiveni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRASecurityPerspective
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- alignes With op security
- alignes With op BDVA Cybersecurity and Trust
- alignes With op FIWARE Security
- alignes With op IDS RAM Security Perspective
- alignes With op IIRA Security
- alignes With op IIC Security Framework
- alignes With op IoT-A Trust Security and Privacy
- alignes With op OCF Security
- frames op Availability
- frames op Identification
- frames op Integrity Protection and Verification
- frames op Privacy
- frames op Service Access Control
- frames op Trustworthiness
OpenFog Security Pillarni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRASecurityPillar
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
- alignes With op security
- alignes With op BDVA Cybersecurity and Trust
- alignes With op FIWARE Security
- alignes With op IDS RAM Security Perspective
- alignes With op IIRA Security
- alignes With op IIC Security Framework
- alignes With op IoT-A Trust Security and Privacy
- alignes With op OCF Security
- alignes With op open fog security perspective
- frames op Security
OpenFog System Architecture Viewni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRASystemView
- belongs to
- Viewpoint c
- has facts
- is Described in op OpenFog Reference Architecture
- frames op Physical Connectivity
ORION Context Brokerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OrionContextBroker
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- associated with op FIWARE Architecture
Performanceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Performance
- belongs to
- Concern c
- has facts
- supports op Business Context
- has wikipedia article dp performance
Performance and Scale Perspectiveni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#OFRAPerformancePerspective
- belongs to
- Standard Classification c
- has facts
- is Described in op OpenFog Reference Architecture
Periodic Communicationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#PeriodicCommunication
- belongs to
- Concern c
- has facts
- supports op Event-Driven Messaging
Physical Connectivityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#PhysicalConnectivity
- belongs to
- Concern c
- has facts
- supports op Interoperability
Physical Webni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#PhysicalWeb
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp faq
Platform Industry 4.0ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#PlatformIndustry40
- belongs to
- organization c
- i io t consortium c
- has facts
- associated with op r a m i
Privacyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Privacy
- belongs to
- Concern c
- has facts
- supports op Data Sovereignty
- supports op Trustworthiness
- has d bpedia resource dp information privacy
Product Liabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ProductLiability
- belongs to
- Concern c
- has facts
- supports op Business Context
Product Managerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ProductManager
- belongs to
- Stakeholder Group c
- Layer c
Programmabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Programmability
- belongs to
- Concern c
- has facts
- is Component Of op Edge computing
- supports op Edge computing
project managerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ProjectManager
- belongs to
- Stakeholder Group c
Provenance Trackingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ProvenanceTracking
Pseudonimityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Pseudonimity
Quality of Serviceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#QualityOfService
- belongs to
- Concern c
- has facts
- supports op Service Description
- has d bpedia resource dp quality of service
r a m i assetlayer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIAssetlayerAnno
- belongs to
- oa annotation c
r a m i body annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIBodyAnno
- belongs to
- oa annotation c
r a m i business layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIBusinessLayerAnno
- belongs to
- oa annotation c
r a m i communicationlayer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMICommunicationlayerAnno
- belongs to
- oa annotation c
r a m i connected worldni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIConnectedWorld
- belongs to
- RAMI Hierarchy Level c
- has facts
- frames op Interoperability
- frames op Semantic Interoperability
- frames op Thing description
r a m i connected world annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIConnectedWorldAnno
- belongs to
- oa annotation c
r a m i control device annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIControlDeviceAnno
- belongs to
- oa annotation c
r a m i enterprise annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIEnterpriseAnno
- belongs to
- oa annotation c
r a m i field deviceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIFieldDevice
- belongs to
- RAMI Hierarchy Level c
- Standard Classification c
- has facts
- frames op manufacturing
r a m i field device annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIFieldDeviceAnno
- belongs to
- oa annotation c
r a m i functional layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIFunctionalLayerAnno
- belongs to
- oa annotation c
r a m i header annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIHeaderAnno
- belongs to
- oa annotation c
r a m i information layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIInformationLayerAnno
- belongs to
- oa annotation c
r a m i integration layer annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIIntegrationLayerAnno
- belongs to
- oa annotation c
r a m i productni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIProduct
- belongs to
- RAMI Hierarchy Level c
- Standard Classification c
- has facts
- frames op manufacturing
r a m i product annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIProductAnno
- belongs to
- oa annotation c
r a m i station annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIStationAnno
- belongs to
- oa annotation c
r d fni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RDF
- belongs to
- document c
- Publication
- Technical Specification c
Radio activity controlni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RadioActivityControl
- belongs to
- Concern c
- has facts
- supports op Energy Control
RAMI Asset Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIAssetlayer
- belongs to
- RAMI IT Layer c
- Standard Classification c
- has facts
- associated with op lifecycle status
- associated with op Edgecross FA
- associated with op IIRA Physical Systems
- associated with op IoT-A Functional Viewpoint
- associated with op IVI Asset View
- is Described in op r a m i
- alignes With op Edgecross FA
- alignes With op IIRA Physical Systems
- alignes With op IoT-A Functional Viewpoint
- alignes With op IVI Asset View
- frames op communication
- frames op Identification
- frames op Identity Management
- frames op Interoperability
- frames op Security
- frames op Semantic Interoperability
- frames op Thing description
- frames op Thing representation
- frames op Trustworthiness
- frames op Virtual Entity
RAMI Business Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIBusinessLayer
- belongs to
- RAMI IT Layer c
- Standard Classification c
- has facts
- associated with op IDS RAM Business Layer
- associated with op IDS RAM Governance Perspective
- associated with op IIRA Business Domain
- associated with op IVI Business Layer
- is Described in op r a m i
- alignes With op IDS RAM Business Layer
- alignes With op IDS RAM Governance Perspective
- alignes With op IIRA Business Domain
- alignes With op IVI Business Layer
- frames op process planning
- frames op Business Context
- frames op Service Composition
- frames op Service Orchestration
RAMI Communication Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMICommunicationlayer
- belongs to
- RAMI IT Layer c
- Standard Classification c
- has facts
- associated with op FIWARE IoT Services Enablement
- associated with op IDS RAM System Layer
- associated with op IIRA Connectivity
- associated with op IIRA Distributed Data Management
- associated with op IoT-A Information Viewpoint
- is Described in op r a m i
- alignes With op FIWARE IoT Services Enablement
- alignes With op IDS RAM System Layer
- alignes With op IIRA Connectivity
- alignes With op IIRA Distributed Data Management
- alignes With op IoT-A Information Viewpoint
- frames op Data Access
- frames op Endpoint Invocation
- frames op Interoperability
- frames op Provenance Tracking
- frames op Security
- frames op Syntactic Interoperability
- frames op Trustworthiness
RAMI Functional Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIFunctionalLayer
- belongs to
- RAMI IT Layer c
- Standard Classification c
- has facts
- associated with op BDVA Data Analytics
- associated with op bdva data viualisation and user interaction
- associated with op DTP System
- associated with op IDS RAM Process Layer
- associated with op IIRA Application Domain
- associated with op IIRA Operation Domain
- associated with op IoT-A Functional Viewpoint
- associated with op IVI Management View
- associated with op NGSI-LD Data Representation
- associated with op Ocean Protocol System Viewpoint
- associated with op x-road System Components
- is Described in op r a m i
- alignes With op BDVA Data Analytics
- alignes With op bdva data viualisation and user interaction
- alignes With op DTP System
- alignes With op IDS RAM Process Layer
- alignes With op IIRA Application Domain
- alignes With op IIRA Operation Domain
- alignes With op IoT-A Functional Viewpoint
- alignes With op IVI Management View
- alignes With op NGSI-LD Data Representation
- alignes With op Ocean Protocol System Viewpoint
- alignes With op x-road System Components
- frames op Endpoint Description
- frames op Interoperability
- frames op Role Categorization
- frames op Semantic Interoperability
- frames op Service Description
RAMI Information Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIInformationLayer
- belongs to
- RAMI IT Layer c
- Standard Classification c
- has facts
- associated with op BDVA Data Analytics
- associated with op BDVA Data Management
- associated with op Edgecross Edgecomputing Layer
- associated with op IDS RAM Information Layer
- associated with op IIRA Application Domain
- associated with op information domain
- associated with op NGSI-LD Information Model
- is Described in op r a m i
- alignes With op BDVA Data Analytics
- alignes With op BDVA Data Management
- alignes With op Edgecross Edgecomputing Layer
- alignes With op IDS RAM Information Layer
- alignes With op IIRA Application Domain
- alignes With op information domain
- alignes With op NGSI-LD Information Model
- frames op Data Analytics
- frames op Data Description
- frames op Data Processing
- frames op Integrity Protection and Verification
- frames op Interoperability
- frames op Security
- frames op Semantic Interoperability
- frames op Stream processing
- frames op Trustworthiness
RAMI Integration Layerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAMIIntegrationLayer
- belongs to
- RAMI IT Layer c
- Standard Classification c
- has facts
- associated with op DTP System
- associated with op Edgecross Edgecomputing Layer
- associated with op Edgecross IT Systems Layer
- associated with op FIWARE IoT Services Enablement
- associated with op IDS RAM System Layer
- associated with op IIRA Control Domain
- associated with op IoT-A Evolution and Interoperability
- associated with op NGSI-LD Architecture
- associated with op x-road Deplyoment View
- associated with op x-road Protocols and Interfaces
- is Described in op r a m i
- alignes With op DTP System
- alignes With op Edgecross Edgecomputing Layer
- alignes With op Edgecross IT Systems Layer
- alignes With op FIWARE IoT Services Enablement
- alignes With op IDS RAM System Layer
- alignes With op IIRA Control Domain
- alignes With op IoT-A Evolution and Interoperability
- alignes With op NGSI-LD Architecture
- alignes With op x-road Deplyoment View
- alignes With op x-road Protocols and Interfaces
- frames op Interoperability
- frames op Semantic Interoperability
- frames op Thing description
- frames op Thing representation
- frames op User Interaction
RAMLni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RAML
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp http://raml.org/
Reactive Streamsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ReactiveStreams
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp http://www.reactive-streams.org/
Real Time Analyticsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RealTimeAnalytics
- belongs to
- Concern c
- has facts
- supports op Data Analytics
- has d bpedia resource dp real time computing
Regulatory Complianceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Regulatory_Compliance
- belongs to
- Concern c
- has facts
- has wikipedia article dp regulatory compliance
Reliabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Reliability
- belongs to
- Concern c
- has facts
- supports op Trustworthiness
- has d bpedia resource dp reliability (computer networking)
Resilienceni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Resilience
- belongs to
- Concern c
- has facts
- supports op Trustworthiness
- has d bpedia resource dp resilience (network)
RESTni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#REST
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- associated with op DTP Deployment
- has wikipedia article dp representational state transfer
Return On Investmentni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ReturnOnInvestment
- belongs to
- Concern c
- has facts
- supports op Business Context
RFC 1122ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_1122
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op i e t f
- has Classification op IIRA Connectivity
- has Classification op network layer
- has Publisher op i e t f
- has official resource dp rfc1122
RFC 5246ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_5246
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op i e t f
- has Classification op Data Sovereignty
- has Classification op IDS RAM Security Perspective
- has Publisher op i e t f
- has official resource dp rfc5246
RFC 6750ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_6750
- belongs to
- document c
- Publication
- Standard c
- has facts
- associated with op Data Transfer Project Architecture
- maker op i e t f
- has Classification op IDS RAM Security Perspective
- has Publisher op i e t f
- has d bpedia resource dp o auth
- has official resource dp rfc6750
RFC 7252ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_7252
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op i e t f
- has Classification op IIRA Operation Domain
- has Classification op tansport layer
- has Publisher op i e t f
- has Publication Date dp "2014-06-01"^^date
- has official resource dp rfc7252
RFC 7642ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_7642
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op i e t f
- has Classification op FIWARE Security
- has Developer op i e t f
- has Publisher op i e t f
- has official resource dp draft ietf scim use cases 08
- has Target Concern op Identity Management
RFC 7643ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_7643
- belongs to
- document c
- Publication
- Standard c
- has facts
- maker op i e t f
- has Classification op FIWARE Security
- has Developer op i e t f
- has Publisher op i e t f
- has official resource dp draft ietf scim core schema 22
- has Target Concern op Identity Management
RFC 7644ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_7644
- belongs to
- Standard c
- has facts
- maker op i e t f
- has Classification op FIWARE Security
- has Developer op i e t f
- has Publisher op i e t f
- has official resource dp draft ietf scim api 19
- has Target Concern op Identity Management
RFC 768ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_768
- belongs to
- Standard c
- has facts
- maker op i e t f
- has Classification op tansport layer
- has Publisher op i e t f
- has d bpedia resource dp user datagram protocol
- has official resource dp rfc768
- has wikipedia article dp user datagram protocol
RFC 793ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RFC_793
- belongs to
- Standard c
- has facts
- maker op i e t f
- has Classification op IDS RAM System Layer
- has Classification op tansport layer
- has Publisher op i e t f
- has official resource dp rfc793
Risk Managementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RiskManagement
- belongs to
- Concern c
- has facts
- supports op Business Context
- has d bpedia resource dp risk management
- has wikipedia article dp risk management
Role Categorizationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RoleCategorization
- belongs to
- Concern c
- has facts
- supports op Identity Management
ROLLni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ROLL
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has official resource dp https://datatracker.ietf.org/wg/roll/
RPMAni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#RPMA
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- has wikipedia article dp random phase multiple access
Safetyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Safety
- belongs to
- Concern c
- has facts
- supports op Trustworthiness
- has d bpedia resource dp safety
Scalabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Scalability
- belongs to
- Concern c
- has facts
- has d bpedia resource dp scalability
SCIMni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SCIM
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- associated with op FIWARE Security
- associated with op RFC 7642
- associated with op RFC 7643
- associated with op RFC 7644
- maker op i e t f
- has Publisher op i e t f
- has d bpedia resource dp system for cross domain identity management
- has wikipedia article dp system for cross domain identity management
- has Target Concern op Cross-domain Identity Management
Secure Communicationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SecureCommunication
- belongs to
- Concern c
- has facts
- supports op communication
- supports op Integrity Protection and Verification
Securityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Security
Security Configurationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SecurityConfiguration
Selection of Service Providerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SelectionOfServiceProvider
- belongs to
- Concern c
- has facts
- supports op Business Context
- supports op Cloud Computing Capability
- has wikipedia article dp service provider
Semantic Interoperabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SemanticInteroperability
- belongs to
- Concern c
- has facts
- supports op Interoperability
- has d bpedia resource dp semantic interoperability
Sensingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Sensing
Service Access Controlni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceAccessControl
- belongs to
- Concern c
- has facts
- associated with op Data Access Control
- supports op authorization
- has d bpedia resource dp network access control
Service Choreographyni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceChoreography
- belongs to
- Concern c
- has facts
- supports op Service Composition
- has d bpedia resource dp service choreography
Service Compositionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceComposition
- belongs to
- Concern c
- has facts
- supports op interoperability
- has d bpedia resource dp service composition
Service Deploymentni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceDeployment
- belongs to
- Concern c
- has facts
- supports op Service life-cycle management
- has d bpedia resource dp software deployment
Service Descriptionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceDescription
- belongs to
- Concern c
- has facts
- supports op Semantic Interoperability
Service Discoveryni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceDiscovery
- belongs to
- Concern c
- has facts
- has d bpedia resource dp service discovery
Service Isolationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceIsolation
- belongs to
- Concern c
- has facts
- has d bpedia resource dp process isolation
Service level agreementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceLevelAgreements
- belongs to
- Concern c
- has facts
- supports op Service life-cycle management
- has d bpedia resource dp service level agreement
Service life-cycle managementni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceLifecycleManagement
- belongs to
- Concern c
- has facts
- has d bpedia resource dp information lifecycle management
Service Orchestrationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceOrchestration
- belongs to
- Concern c
- has facts
- supports op Service Composition
- has d bpedia resource dp orchestration (computing)
- has wikipedia article dp deployment
- has wikipedia article dp orchestration (computing)
Service Recoveryni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Service_Recovery
- belongs to
- Concern c
- has facts
- supports op Cloud Computing Capability
- supports op Reliability
- has wikipedia article dp service recovery
Service Selectionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ServiceSelection
- belongs to
- Concern c
- has facts
- supports op Service Composition
Software Updatesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Software_Updates
- belongs to
- Concern c
- has facts
- supports op Evolvability
- has wikipedia article dp wikipedia: software updates
Spatial modelingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SpatialModeling
- belongs to
- Concern c
- has facts
- supports op Data Description
- supports op Semantic Interoperability
- has d bpedia resource dp spatial analysis
Stream processingni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#StreamProcessing
- belongs to
- Concern c
- has facts
- supports op Data Processing
- has d bpedia resource dp stream processing
Syntactic Interoperabilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SyntacticInteroperability
- belongs to
- Concern c
- has facts
- supports op Interoperability
- has wikipedia article dp syntactic interoperability
System Engineerni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SystemEngineer
- belongs to
- Stakeholder Group c
- Layer c
System evolutionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SystemEvolution
- belongs to
- Concern c
- has facts
- supports op Evolvability
- has d bpedia resource dp software evolution
system operatorni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SystemOperator
- belongs to
- Stakeholder Group c
System Recoveryni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#SystemRecovery
- belongs to
- Concern c
- has facts
- supports op Reliability
The Industrial Internet of Things Volume G1: Reference Architecture IIC:PUB:G1:V1.80:20170131ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#IIC_PUB_G1_V1_80_20170131
- belongs to
- oa specific resource c
The Industrial Internet of Things Volume G5: Connectivity Framework ni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#The_Industrial_Internet_of_Things_Volume_G5_Connectivity_Framework
- belongs to
- oa specific resource c
Thing descriptionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ThingDescription
- belongs to
- Concern c
- has facts
- supports op Semantic Interoperability
Thing mobilityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ThingMobility
- belongs to
- Concern c
- has facts
- supports op Data Access
- supports op IoT
- supports op Service Deployment
Thing representationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#ThingRepresentation
Time Synchronizationni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#TimeSynchronization
- belongs to
- Concern c
- has facts
- supports op Service Composition
- has d bpedia resource dp "Synchronization refers to one of two distinct but related concepts: synchronization of processes, and synchronization of data. Process synchronization refers to the idea that multiple processes are to join up or handshake at a certain point, in order to reach an agreement or commit to a certain sequence of action. Data synchronization refers to the idea of keeping multiple copies of a dataset in coherence with one another, or to maintain data integrity. Process synchronization primitives are commonly used to implement data synchronization. (sourc: wikipedia)"@en
- has d bpedia resource dp synchronization (computer science)
Trusted Connectorni back to ToC or Named Individual ToC
IRI: https://w3id.org/ids/core/TrustedConnector
- belongs to
- Technology c
- has facts
- associated with op Administration Shell
- associated with op IDS RAM
- maker op IDS RAM
- alignes With op Administration Shell
Trustworthinessni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Trustworthiness
- belongs to
- Concern c
- has facts
- has d bpedia resource dp software trustworthiness
Unicastni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#Unicast
- belongs to
- Concern c
- has facts
- supports op cardinality of data sources
Unreliable Networkni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#UnreliableNetwork
- belongs to
- Concern c
- has facts
- supports op Reliability
User Interactionni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#UserInteraction
- belongs to
- Concern c
- has facts
- supports op user experience
- has d bpedia resource dp interaction design
User Preferencesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#UserPreferences
- belongs to
- Concern c
- has facts
- supports op Service level agreement
Vendor Lockinni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#VendorLockin
- belongs to
- Concern c
- has facts
- supports op Business Context
- supports op Cloud Computing Capability
- has wikipedia article dp vendor lock in
Virtual Entityni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#VirtualEntity
- belongs to
- Concern c
- has facts
- supports op Thing representation
- has d bpedia resource dp digital twin
x a c m lni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#XACML
- belongs to
- document c
- Publication
- Technical Specification c
- has facts
- associated with op FIWARE Security
- has Target Concern op authorization
- has Target Concern op Data Access Control
x road deployment view annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#xRoadDeploymentViewAnno
- belongs to
- oa annotation c
x road protocols interfaces annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#xRoadProtocolsInterfacesAnno
- belongs to
- oa annotation c
x road system components annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#xRoadSystemComponentsAnno
- belongs to
- oa annotation c
x road technology matrix annoni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#xRoadTechnologyMatrixAnno
- belongs to
- oa annotation c
x-roadni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#x-road
- belongs to
- Data Sharing Initiative c
X-Road Architecture Technical Specification Version: 1.0 18.09.2015 15 pages Doc. ID: ARC-Gni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#X_Road_Architecture_Technical_Specification
- belongs to
- oa specific resource c
x-road Deplyoment Viewni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#xRoadDeploymentView
- belongs to
- Standard Classification c
- x-road Section c
- has facts
- associated with op IDS RAM System Layer
- associated with op IIRA Implementation Viewpoint
- associated with op RAMI Integration Layer
- is Described in op x-Tee
- alignes With op IDS RAM System Layer
- alignes With op IIRA Implementation Viewpoint
- alignes With op RAMI Integration Layer
- frames op communication
- frames op Data Access
- frames op Security
- frames op Service Deployment
- frames op Service life-cycle management
- frames op Trustworthiness
x-road Protocols and Interfacesni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#xRoadProtocolsInterfaces
- belongs to
- Standard Classification c
- x-road Section c
- has facts
- associated with op IDS RAM Process Layer
- associated with op IIRA Control Domain
- associated with op RAMI Integration Layer
- is Described in op x-Tee
- alignes With op IDS RAM Process Layer
- alignes With op IIRA Control Domain
- alignes With op RAMI Integration Layer
- frames op communication
- frames op Interoperability
- frames op Syntactic Interoperability
x-road System Componentsni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#xRoadSystemComponents
- belongs to
- Standard Classification c
- x-road Section c
- has facts
- associated with op IDS RAM Business Layer
- associated with op IDS RAM Process Layer
- associated with op IIC Security Framework
- associated with op RAMI Functional Layer
- is Described in op x-Tee
- alignes With op IDS RAM Business Layer
- alignes With op IDS RAM Process Layer
- alignes With op IIC Security Framework
- alignes With op RAMI Functional Layer
- frames op Authentication
- frames op communication
- frames op Identity Management
- frames op Secure Communication
- frames op Security
- frames op Security Configuration
- frames op Trustworthiness
x-road Technology Matrixni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#xRoadTechnologyMatrix
- belongs to
- Standard Classification c
- x-road Section c
- has facts
- is Described in op x-Tee
x-Teeni back to ToC or Named Individual ToC
IRI: https://w3id.org/i40/sto#xTee
- belongs to
- Architecture Description c
- Standarization Framework c
- has facts
- has Publisher op x-road
Legend back to ToC
op: Object Properties
dp: Data Properties
ni: Named Individuals
References back to ToC
- Grangel-Gonzalez Irlan, Paul Baptista, Lavdim Halilaj, Steffen Lohmann, Maria-Esther Vidal, Cristian Mader, Soeren Auer, The industry 4.0 standards landscape from a semantic integration perspective, in: 22nd IEEE International Conference on Emerging Technologies and Factory Automation, ETFA, Limassol, Cyprus, September 12-15, 2017, pp. 1–8.
- Lu, K. C. Morris, S. Frechette, Standards landscape and directions for smart manufacturing systems, in: IEEE International Conference on Automation Science and Engineering, CASE, Gothenburg, Sweden, August 24-28, 2015, pp. 998–1005.
- S.-W. Lin, B. Murphy, E. Clauer, U. Loewen, R. Neubert, G. Bachmann,M. Pai, M. Hankel, Reference Architectural Model Industrie 4.0 (RAMI4.0), Tech. rep., Industrial Internet Consortium and Plattform Industrie4.0 (2017).
Acknowledgements back to ToC




